What Is SOC 2 Type 2: what is soc type 2 and Why It Matters for SaaS

Let’s get straight to it. A SOC 2 Type 2 report is the gold standard for proving your company’s security controls actually work—not just on paper, but consistently over a long period of time.
Think of it like this: a Type 1 report is like taking a single photo of a clean house. A Type 2 report is like having a home inspector live with you for a year, verifying that you keep it clean every single day. That’s the level of proof that builds real trust with customers.
What Is A SOC 2 Type 2 Report, Really?

A SOC 2 Type 2 report isn’t just a certificate you hang on the wall. It’s a detailed audit, based on standards from the American Institute of Certified Public Accountants (AICPA), that tests how your security controls operate over a specific timeframe, usually between six and twelve months.
This focus on operational effectiveness is what really matters. It moves beyond theory and into practice, proving that your security isn’t just a policy—it’s a habit.
This kind of verification has become table stakes. With cybersecurity threats on the rise and regulations like GDPR and HIPAA getting stricter, companies are under more pressure than ever to prove they can be trusted with sensitive data.
Here’s a quick breakdown of what a SOC 2 Type 2 report covers.
SOC 2 Type 2 At A Glance
| Attribute | Description |
|---|---|
| Focus | Evaluates the operational effectiveness of security controls over time. |
| Timeframe | Covers a specific observation period, typically 6 to 12 months. |
| Output | A detailed audit report with the auditor’s opinion and test results. |
| Audience | Intended for customers, partners, and stakeholders under NDA. |
| Core Value | Provides deep, evidence-based assurance of sustained security practices. |
This table highlights why the Type 2 report is so valuable—it’s not a one-off check, but a continuous validation of your security posture.
Why This Report Is Essential For Business Growth
For any company in SaaS, FinTech, or HealthTech, a SOC 2 Type 2 report has become a key to unlocking enterprise sales. It’s the universal language of security that answers the tough questions from sophisticated buyers before they even have to ask.
Instead of just saying “we’re secure,” a SOC 2 Type 2 report provides independent, third-party validation that says, “we’ve proven we’re secure, every day, for the last six months.” This is the evidence-based approach that enterprise clients demand.
Going through the audit process forces a level of operational discipline that strengthens your entire organization. It helps you:
- Accelerate Sales Cycles: A clean SOC 2 report can replace massive security questionnaires, immediately removing a major roadblock in your sales process.
- Build Real Customer Confidence: It demonstrates you are a serious, responsible steward of their data, which dramatically reduces their perceived risk of doing business with you.
- Gain a Competitive Edge: In a crowded market, having your SOC 2 Type 2 report ready can be the deciding factor that proves your reliability and trustworthiness over a competitor.
To see how companies communicate this commitment, check out their security pages, which are often found in a dedicated Trust Center. At the end of the day, getting a SOC 2 Type 2 report isn’t just about checking a compliance box; it’s about building a rock-solid foundation of operational excellence that fuels your growth.
SOC 2 Type 1 vs. Type 2: What’s the Difference?
Understanding the difference between a SOC 2 Type 1 and Type 2 report is one of the first hurdles for companies new to compliance. It’s a common point of confusion, but the distinction is actually pretty simple.
Let’s use an analogy. Imagine you’re building a state-of-the-art security system for your office.
A Type 1 report is like the architect’s blueprint. An auditor reviews your plans and confirms that, on paper, the system is designed correctly to meet the required security standards. It’s a snapshot, a picture taken at a single point in time.
A Type 2 report, on the other hand, is like a long-term stress test. The auditor doesn’t just glance at the blueprint; they move into the building for six months, watching the system operate day in and day out. They test the cameras during a thunderstorm, check the locks at midnight, and verify the guards are actually at their posts. This is what we mean by testing operational effectiveness.
The Blueprint vs. The Live Feed
A SOC 2 Type 1 audit assesses the design of your security controls at a specific moment. The auditor’s key question is: “Are your controls designed appropriately to meet the relevant Trust Services Criteria?” It’s a fantastic first step that helps you establish a solid security baseline.
In contrast, a SOC 2 Type 2 audit examines both the design and the operating effectiveness of your controls over a period of time, usually between six and twelve months. The auditor asks a much tougher question: “Did your controls actually work as intended, consistently, over this entire period?”
A Type 1 report says, “We have a good plan.” A Type 2 report proves, “Our plan works in the real world, and we have the logs and records to back it up.” This distinction is critical for enterprise customers who need proof, not just promises.
Many companies strategically start with a Type 1 report. It allows them to identify and fix any design flaws in a controlled way before committing to the longer, more demanding Type 2 observation period. This approach often saves a lot of headaches and reduces the risk of getting a negative audit opinion down the line. For a deeper dive, check out our complete guide to SOC 2 Type 2 vs Type 1.
Comparing The Two Reports Side-by-Side
To make the differences crystal clear, let’s break down the key attributes of each report in a simple table.
Comparing SOC 2 Reports Type 1 vs Type 2
This table lays out the core differences to help you quickly see which report fits your current needs.
| Feature | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Objective | Assesses the design of controls. | Assesses both the design and operational effectiveness of controls. |
| Timeframe | A single point in time (e.g., as of June 30). | Over a period of time (e.g., January 1 to June 30). |
| Evidence Required | Policy documents, system configurations, process descriptions. | All Type 1 evidence, plus logs, change records, and meeting minutes. |
| Customer Value | Provides initial assurance that a security program is well-designed. | Provides deep assurance that security is a sustained, operational practice. |
Ultimately, while a Type 1 report can open doors, a Type 2 is what closes the deal with large, security-conscious customers. It provides the high level of assurance they require to trust you with their sensitive data.
Breaking Down The Five Trust Services Criteria
The entire SOC 2 framework is built on five core principles known as the Trust Services Criteria (TSC). Think of them as the building blocks of your security program. But here’s the key: you don’t necessarily need all five. Your business model and the specific promises you make to your customers dictate which ones you’ll need to include in your audit.
Every single SOC 2 audit, without exception, starts with the Security criterion. This one is non-negotiable. Often called the Common Criteria, it’s the foundation that proves your systems and data are protected from unauthorized access, funny business, or flat-out theft. It’s the baseline—covering everything from access controls and firewalls to vulnerability management.
Once you have Security covered, you’ll choose from the other four criteria based on what’s relevant to your service commitments.
Choosing Your Additional Criteria
The other four criteria—Availability, Processing Integrity, Confidentiality, and Privacy—are selected based on the promises you make in your customer contracts and Service Level Agreements (SLAs). You only add the criteria that directly map to how your business operates and what you guarantee your customers.
For a deeper dive into each one, check out our complete guide to the SOC 2 Trust Services Criteria.
Here’s how they shake out in the real world:
-
Availability: Do you guarantee a certain level of uptime? If your SLA promises 99.9% availability, you need this criterion. It proves you have the right controls for performance monitoring, disaster recovery, and incident response to actually deliver on that promise.
-
Processing Integrity: This one is critical if your service handles transactions that need to be complete, accurate, and on time. Think of an e-commerce platform processing payments or a fintech app calculating loan interest—Processing Integrity is the proof that the system does what it says it will do, without errors.
-
Confidentiality: If you handle sensitive information that must be kept under wraps, this is your criterion. A virtual data room for mergers and acquisitions is a perfect example; Confidentiality proves that only the right people can access highly sensitive M&A documents.
-
Privacy: This is different from Confidentiality. Privacy is all about how you collect, use, and dispose of Personally Identifiable Information (PII). If your service handles customer data that falls under regulations like GDPR or CCPA, the Privacy criterion shows your processes align with your privacy notice and legal standards.
The Evolving Demands of Compliance
Picking the right TSCs is more than a simple box-checking exercise, especially as the compliance world keeps changing. The AICPA has updated its guidance to address modern threats, putting a much stronger emphasis on continuous monitoring. They recognize that a once-a-year checkup just doesn’t cut it anymore in a world of persistent AI-driven attacks and cloud misconfigurations.
Today, what is SOC 2 Type 2 really about? It’s about proving ongoing diligence. The standard has evolved to require more frequent control testing, often monthly, to provide meaningful assurance.
This higher standard is a direct response to a much riskier digital environment. It’s not just a suggestion; it’s the new expectation. Globally, 92% of organizations now conduct two or more audits each year, and a staggering 58% run four or more just to keep up. Enterprises are also tightening the screws, with many requiring vendor reports to be less than 90 days old to be considered valid.
Choosing your TSCs is a strategic decision. It aligns your audit directly with your business promises, answers customer security questions before they’re even asked, and shows you have a mature grasp on your responsibilities in a world where security is everything.
Breaking Down The SOC 2 Type 2 Audit Process
Getting a SOC 2 Type 2 report can feel like a marathon, not a sprint. The best way to tackle it is to break the journey down into clear, manageable phases. This turns a massive project into a series of achievable steps, keeping your team focused and setting you up for a successful audit.
Honestly, the real work begins long before your auditor even shows up. It starts with taking a hard look in the mirror to figure out where you really stand.
Phase 1: Readiness Assessment
First up is the Readiness Assessment. Think of this as a dress rehearsal or a friendly pre-audit. You’ll work with a qualified auditor or consultant to pinpoint all the gaps between your current security controls and what SOC 2 actually requires for your chosen Trust Services Criteria.
This is your golden opportunity to find and fix issues before they become a real problem in your final report. Trust me, it’s a lot cheaper and less stressful to patch a weak control during this phase than to have it flagged as an official “exception” by your auditor.
This stage usually involves:
- Scoping: Nailing down exactly which systems, processes, and Trust Services Criteria are in-scope for the audit.
- Gap Analysis: A detailed comparison of your existing policies and controls against the specific requirements of the SOC 2 framework.
- Reporting: You’ll get a report that highlights what you’re doing well and, more importantly, a prioritized punch list of weaknesses you need to fix.
Phase 2: Remediation
With the findings from your readiness assessment in hand, you move into the Remediation phase. This is where you roll up your sleeves and get to work fixing those identified gaps. Remediation isn’t just about applying a software patch; it’s about fundamentally improving your security posture.
For a more granular look at the steps involved, from scoping to implementing controls, check out this excellent technical guide on how to get SOC 2 certification.
This simple diagram shows how the core Trust Services Criteria are layered.
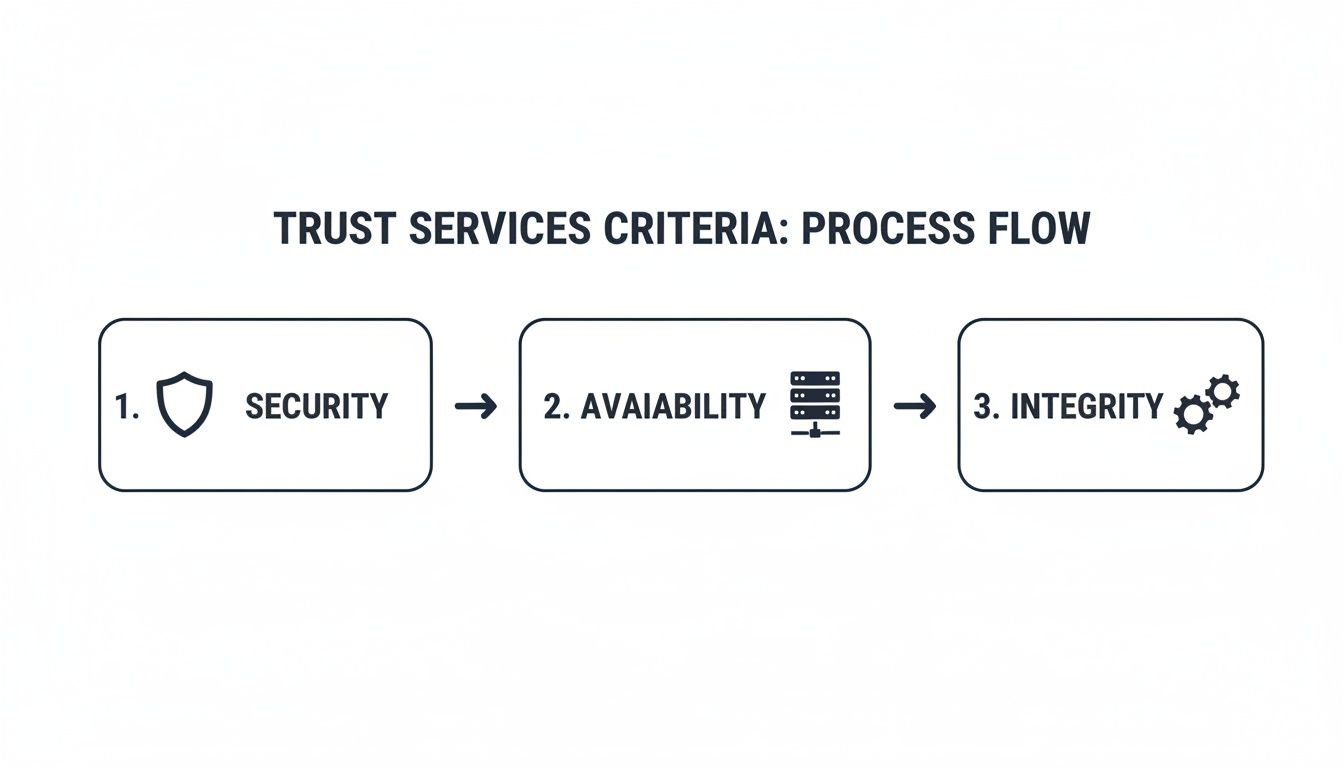
As you can see, every audit is built on the foundation of the Security criterion. From there, you might add Availability or Integrity depending on the specific promises you make to your customers.
Phase 3: The Observation Period and Evidence Collection
Once your controls are implemented and humming along, the official Observation Period kicks off. For a Type 2 report, this is typically a 6 to 12-month window where your controls need to be working consistently. This is the main event—where you prove your security program isn’t just a one-and-done setup.
This phase is the very heart of a SOC 2 Type 2 audit. It’s not enough to have a control; you have to generate and collect evidence that proves the control was working effectively, day in and day out, for the entire observation period.
During this time, your team is on the hook for continuous Evidence Collection. You’re constantly gathering proof that your controls are doing their job. Auditors will later ask for samples from this period to perform their testing.
A few examples of critical evidence include:
- Access Logs: Who logged into sensitive systems and when? You need the records to prove it.
- Change Management Tickets: Documentation showing every single change to your production environment was properly approved and tested.
- Vulnerability Scans: Regular reports from your scanning tools that identify potential security holes.
- Employee Training Records: Proof that your team has actually completed their required security awareness training.
By moving through these phases methodically, you can manage your resources, set realistic deadlines, and guide your team toward a clean SOC 2 Type 2 report that actually means something.
Budgeting For Your SOC 2 Type 2 Audit
When you start planning for a SOC 2 Type 2 audit, two questions jump to the front of the line: “How much is this going to cost?” and “How long will this take?” It’s natural to focus on these, but the key is to see the process not as a simple expense, but as a strategic investment that unlocks real business growth.
The timeline to get your SOC 2 Type 2 report can be anywhere from three to twenty months. That’s a huge range, right? It all depends on how much heavy lifting you need to do during the initial readiness and remediation phases. After that, you have the mandatory observation period, which itself is typically six to twelve months long.
Understanding SOC 2 Audit Costs
Let’s be clear: there’s no single price tag for a SOC 2 Type 2 audit. Costs can run from $15,000 for a small, simple startup to well over $400,000 for a massive, complex enterprise. The final number comes down to a few key drivers you need to have on your radar.
Several factors will directly influence your audit bill:
- Company Size and Complexity: More employees, more systems, and more data centers mean more controls to test. More controls mean more work for the auditor, which means a higher cost. Simple as that.
- Audit Scope: If you’re adding Trust Services Criteria beyond the mandatory Security principle, you’re adding complexity and cost with each one.
- System Maturity: A company that already has a well-documented, mature security program will have a much smoother—and cheaper—audit than one that’s starting from square one.
- Choice of Audit Firm: Boutique, specialized firms often provide more competitive pricing. The “Big Four” accounting firms, on the other hand, might offer more brand recognition in certain markets, but it comes at a premium.
For a deeper dive into all the variables, our guide breaks down everything that influences how much a SOC 2 audit costs.
The Strategic Value of Your Investment
Thinking about this purely as a cost is missing the bigger picture. A SOC 2 Type 2 report is a powerful tool for your business. It can shorten sales cycles, build unbreakable trust with enterprise clients, and forge a powerful, defensible security posture. In a market where security is everything, it’s a massive competitive advantage.
Think of your SOC 2 audit less as a tax and more as a growth lever. It’s the key that unlocks larger deals and moves your company upmarket by answering the toughest security questions before they are even asked.
This investment is also a direct response to what the market demands. The global market for SOC services is projected to hit $10.5 billion by 2030 for a reason. With 58% of organizations now conducting four or more audits a year to prove their resilience, it’s clear that this level of verification has become the standard for building customer confidence. You can discover more insights about these compliance statistics to see how they’re shaping modern security expectations.
Finding The Right SOC 2 Auditor For Your Business
Choosing the right audit firm is one of the most critical decisions you'll make in your entire SOC 2 Type 2 journey. This single choice directly impacts your final cost, the project timeline, and your team's stress levels.Pick the wrong partner, and you’re looking at painful delays, surprise costs, and a report that doesn’t quite hit the mark with your key customers. The right firm, on the other hand, is a genuine partner. They get your business, whether you’re in SaaS, FinTech, or HealthTech, and have a proven track record with companies just like yours.
Picking an auditor isn’t about finding any certified CPA; it’s about finding an expert who understands your world.
Key Criteria For Selecting Your Auditor
Before you even think about signing an engagement letter, you need to vet potential firms on a few critical factors. Rushing this step is a classic mistake that can haunt your compliance program for years.
Here’s where to focus your evaluation:
- Industry Specialization: Do they have deep experience in your vertical? An auditor who lives and breathes the unique risks of a SaaS platform is going to be far more effective than a generalist.
- Company Size Experience: A firm that mostly serves massive enterprises might not be the right fit for a fast-growing startup, and vice-versa. You need a partner who understands your operational reality.
- Reputation and Client Feedback: Look for transparent reviews and don’t be shy about asking for references. A firm’s reputation is built on its history of delivering clear, useful, and respected audit reports.
Historically, this has been a frustrating process. You’d have to rely on word-of-mouth, deal with opaque pricing, and sit through endless, time-consuming sales calls. The lack of clear, comparable data makes it almost impossible to know if you’re getting a fair price or the right partner.
Making a Data-Driven Decision
This is exactly the problem SOC2Auditors.org was built to solve. Instead of navigating a confusing market on your own, the platform gives you transparent, verified data on over 90 different audit firms. It turns a high-stakes guessing game into a structured, data-driven process.
The old way of finding an auditor was broken—it was slow, lacked transparency, and often left companies feeling like they overpaid. The goal should be to find the perfect match for your specific needs, not just the first firm that answers the phone.
With a platform built for this specific purpose, you can sidestep common pitfalls like overpaying or suffering through preventable delays. You can filter firms by your exact budget, desired timeline, and industry focus.
This lets you quickly build a shortlist of ideal partners and receive up to three tailored matches, all without the pressure of a single sales call. The platform empowers you to compare firms side-by-side, so you can make a confident decision that accelerates your path to a successful audit.
Frequently Asked Questions About SOC 2 Type 2
Navigating the world of compliance always brings up questions. Here are some straight, no-nonsense answers to the most common ones we hear.
How Long Is A SOC 2 Type 2 Report Valid For?
Your SOC 2 report doesn’t have a hard expiration date like a carton of milk, but it definitely has a shelf life. Most clients, partners, and especially enterprise customers will not accept a report that’s more than 12 months old.
Think of it like an annual health checkup for your security program. The report only provides assurance for the specific period it covers, so to prove your controls are still working, you need to get a new one every year. It’s just the standard cadence of the industry.
Can You Fail A SOC 2 Type 2 Audit?
Absolutely. In auditor-speak, “failing” means getting a “qualified” or “adverse” opinion on your report. A qualified opinion flags significant issues with one or more controls, while an adverse opinion means the problems are widespread and material. It’s bad news.
This usually happens when an auditor finds major exceptions during testing—for example, if your team consistently skipped mandatory access reviews or didn’t patch critical vulnerabilities on time. The number one reason for failure? Not having enough evidence to prove your controls worked throughout the observation period. This is why being diligent about preparation is so critical.
A clean, “unqualified” opinion is the goal. It’s the auditor’s stamp of approval, confirming your controls are designed appropriately and operated effectively for the entire audit period. Anything less is a red flag for your customers.
Is A Readiness Assessment Necessary Before An Audit?
While it’s not technically required, skipping a readiness assessment is a rookie mistake, especially for your first audit. It’s basically a “pre-audit” or dress rehearsal where a professional finds all the gaps in your controls before the real audit clock starts ticking.
Doing this lets you fix any weaknesses beforehand, which dramatically increases your chances of getting that clean report. Seriously, investing in a readiness assessment almost always saves you a ton of time, money, and headaches down the road by preventing ugly surprises during the actual audit.
What Is The Difference Between SOC 2 And ISO 27001?
People often lump these two together, but they serve different purposes and come from different philosophies.
- SOC 2: This is an attestation report based on the Trust Services Criteria. It’s the standard in North America and gives a detailed opinion on how well your controls actually work in practice. It’s flexible and principles-based.
- ISO 27001: This is a globally recognized certification. It certifies that you’ve built and implemented a comprehensive Information Security Management System (ISMS) according to a very specific, prescriptive standard.
Many global companies end up getting both. They use SOC 2 to satisfy customers in the US and ISO 27001 for partners in the EU and other international markets.
Finding the right auditor is the most critical step in your compliance journey. Instead of navigating an opaque market, SOC2Auditors provides transparent, verified data on over 90 firms, allowing you to filter by budget, timeline, and industry to find your perfect match. Get started today at https://soc2auditors.org.