What Is a SOC 2 Type 2 Report A Guide to Proving Security Over Time

A SOC 2 Type 2 report is an independent auditor’s stamp of approval on how a company’s security controls actually performed over a specific time, usually 3-12 months. It’s the ultimate proof that your security isn’t just a policy on a shelf—it’s a living, breathing practice.
The Definitive Answer to What Is a SOC 2 Type 2 Report

Here’s the best analogy I’ve heard: a SOC 2 Type 1 report is like a single, perfectly staged photo of a secure house. It shows the right locks are on the doors and the alarm system is installed. All the pieces are in place.
A SOC 2 Type 2 report, however, is the continuous security camera footage from the last six months. It proves the doors were consistently locked, the alarms were always armed, and every security rule was followed day in and day out.
That distinction is everything. A Type 2 report gives your customers a much higher level of assurance because it doesn’t just look at the design of your security controls; it verifies their operational effectiveness through rigorous testing over a real-world observation window.
A Deeper Look at the Report’s Purpose
At its core, a SOC 2 Type 2 report is an auditor’s official opinion that a company’s security practices—as they relate to the AICPA’s Trust Services Criteria—are both well-designed and consistently followed. This isn’t just some niche framework; it’s the globally recognized standard for cloud and SaaS companies trying to prove they can be trusted.
The real-world benefit? A recent Type 2 report dramatically reduces sales friction. Handing it over often satisfies the most demanding enterprise security questionnaires, shortening due diligence from weeks to days. If you want to dive into the nuts and bolts, Secureframe has a solid breakdown of the SOC 2 Type 2 methodology.
Ultimately, this report is the gold standard for building client trust. It’s the definitive answer to the questions every potential customer is asking:
- Can I really trust you with my sensitive data?
- Are your security promises just marketing fluff, or are they backed by consistent action?
- Do you have the discipline and processes to protect my information for the long haul?
An unqualified opinion in a Type 2 report is a powerful, third-party “yes” to all three.
SOC 2 Type 2 Report At a Glance
To boil it all down, here’s a quick summary of the key attributes of a SOC 2 Type 2 report. This table highlights what it covers, who it’s for, and why it matters in the real world.
| Attribute | Description |
|---|---|
| Primary Focus | Tests the operational effectiveness of security controls over a period of time (e.g., 6-12 months). |
| Key Question Answered | Do your security controls actually work as intended on a consistent, ongoing basis? |
| Intended Audience | Customers, partners, and stakeholders who need deep assurance about a vendor’s security posture. |
| Business Purpose | To build trust, satisfy enterprise vendor requirements, and accelerate sales cycles by proving security maturity. |
This table makes it clear: a Type 2 report isn’t just about checking a box. It’s a strategic asset for any company serious about earning and keeping customer trust.
Comparing SOC 2 Type 1 and Type 2 Reports

While they sound almost identical, the difference between a SOC 2 Type 1 and a Type 2 report is massive. Getting this wrong means you won’t understand the level of assurance a vendor is actually giving you. It’s the classic difference between a promise and real proof.
Here’s an analogy: think of building a high-security bank vault.
A SOC 2 Type 1 report is like getting an architect to approve your blueprints. The auditor looks at the design of your security controls at a single moment—a “point in time”—and confirms that, on paper, they look solid enough to meet the criteria. It’s a snapshot.
A SOC 2 Type 2 report is like hiring a security team to monitor that vault for an entire year. They don’t just glance at the blueprints; they watch the guards, test the locks daily, and review months of camera footage to prove the vault was never breached. The auditor tests the operational effectiveness of your controls over a sustained period, usually 3 to 12 months.
This is why a search for what is a SOC 2 Type 2 report always circles back to the idea of ongoing proof. It provides hard evidence that your security isn’t just a theory but a day-in, day-out operational reality.
The Point-in-Time Snapshot
A Type 1 report absolutely has its place. It’s a fantastic first step for a company just starting its compliance journey. Many use it as a “readiness assessment” to validate their control design before tackling the more intense Type 2. It’s also faster and cheaper to get.
But its limitation is a big one. It tells you nothing about whether those well-designed controls actually worked yesterday, are working today, or will work tomorrow. A lot can happen after the photo is taken.
The Continuous Security Story
A Type 2 report tells a story over time. An auditor doesn’t just ask, “Do you have a firewall?” They collect evidence to prove that the firewall was properly configured and running without any sketchy changes throughout the entire audit period.
This is exactly why sophisticated customers—especially mid-market and enterprise clients—almost always demand a Type 2. They need to know your security practices are consistent and reliable, not just well-documented for one day of the year.
A Type 1 report shows you have a plan. A Type 2 report proves your plan actually works under real-world conditions, day after day. This distinction is the bedrock of trust in any vendor relationship.
Key Differences Between SOC 2 Type 1 and Type 2 Reports
To make this crystal clear, let’s put them side-by-side. This table breaks down the core differences across the factors that really matter when you’re evaluating a vendor’s security program.
| Factor | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Audit Focus | Design Suitability of controls at a single point in time. | Operational Effectiveness of controls over a period of time. |
| Evidence | Primarily based on documentation, policies, and system descriptions. | Requires extensive evidence of controls operating, like logs and records. |
| Timeline | Faster to complete, as it only covers a specific date. | Longer process, requiring an observation period of 3-12 months. |
| Assurance Level | Provides moderate assurance that controls are designed correctly. | Provides high assurance that controls are designed and working effectively. |
| Best For | Early-stage companies proving initial compliance or internal readiness. | Companies selling to enterprise clients who require proof of ongoing security. |
In the end, while a Type 1 report is a respectable start, the SOC 2 Type 2 report is the true industry standard for showing you have a mature and trustworthy security program. It’s the document that unlocks bigger deals and builds lasting customer confidence.
Breaking Down the Five Trust Services Criteria
At the core of every SOC 2 report are the Trust Services Criteria (TSC). These are five principles the AICPA created to evaluate how a company protects customer data. Think of them like the subjects in your high school curriculum: you have to pass the mandatory classes, but you also pick electives based on what you want to specialize in.
This structure is what makes SOC 2 so practical. It’s not a rigid, one-size-fits-all checklist. Instead, it’s a flexible framework that lets you prove your security where it matters most to your customers.
Each criterion gives an auditor a specific lens to look through when they examine your controls, ensuring the final report is both comprehensive and relevant to the promises you make.
The Mandatory Foundation: Security
The Security criterion is the non-negotiable foundation of every single SOC 2 audit. You can’t get a report without it. It’s often called the “Common Criteria” for this reason. It answers the fundamental question: is your system protected against unauthorized access, use, or modification?
Think of it as the basic security for your house. It covers the essentials everyone expects:
- Access Controls: This is like having strong locks on your doors and windows, making sure only authorized people can get in.
- Firewalls: This is your fence and gate, creating a strong barrier between your private network and the public internet.
- Intrusion Detection: These are your security cameras and alarm systems, alerting you to anything suspicious.
These controls are universal because they form the bedrock of any trustworthy service. Without a solid security foundation, the other criteria are pretty much meaningless.
Choosing Your Additional Criteria
Beyond Security, you get to choose which other TSCs to include based on your business and the commitments you’ve made to customers. This is where you tailor the audit to tell the right story.
For a deeper dive on this, check out our detailed guide on the SOC 2 Trust Services Criteria in our detailed guide.
Let’s break down the other four criteria with some real-world examples.
-
Availability: This one is for services that promise serious uptime. The audit focuses on whether your system is available for use as you’ve agreed. A cloud provider like AWS or a critical tool like Slack would absolutely include Availability to prove they have solid disaster recovery plans and performance monitoring in place.
-
Processing Integrity: This is crucial for any platform that performs calculations or handles transactions. It looks at whether your system processing is complete, valid, accurate, and timely. An e-commerce platform processing payments or a financial analytics tool running complex algorithms needs this to prove their data processing is reliable.
-
Confidentiality: This criterion is all about protecting information that has been specifically designated as confidential. If your service handles intellectual property, sensitive M&A documents, or legal contracts, you’ll need this one. Think of a secure file-sharing service like Dropbox; they use encryption and strict access policies to prove only the right people can see confidential files.
-
Privacy: While it sounds a lot like Confidentiality, Privacy is laser-focused on Personally Identifiable Information (PII). It covers how PII is collected, used, retained, and destroyed. Any company handling customer health records, social security numbers, or other personal data—like a HealthTech platform—must include the Privacy criteria.
Picking the right TSCs is a strategic decision. Adding criteria you don’t need wastes time and money. But leaving out one that your customers expect can make your report look weak. Your choices should directly mirror the promises you make in your contracts and marketing.
How to Actually Read a SOC 2 Type 2 Report
Getting a 100-page SOC 2 Type 2 report from a vendor can feel like homework. It’s dense, technical, and looks like it was written by auditors, for auditors. But you don’t need to be a security guru to pull out the critical information you need to make a smart risk decision.
The secret is knowing where to look and what to look for. The most important stuff isn’t buried on page 73; it’s right up front. Learning to decipher this document lets you move beyond the cover page and truly vet a vendor’s security posture against your own standards.
Start with the Auditor’s Opinion
Before you touch anything else, flip to Section 1: The Independent Auditor’s Report. This is where the CPA firm gives its official verdict on the vendor’s controls. Think of it as the executive summary for the entire report.
You’re hunting for one key phrase: an unqualified opinion. This is the best possible outcome. It means the auditor found that the vendor described their system fairly and their controls were designed properly and actually worked throughout the entire audit period. It’s a clean bill of health.
Anything else is a potential red flag:
- Qualified Opinion: This means the auditor found issues with one or more specific controls, but the rest of the report is fine. It’s a “mostly good, but…” verdict that demands you dig deeper into what went wrong.
- Adverse Opinion: This is a huge deal. It means the auditor found significant, widespread problems and believes the vendor’s controls are fundamentally ineffective. Walk away.
- Disclaimer of Opinion: Also a massive red flag. This means the auditor couldn’t even gather enough evidence to form an opinion, which usually points to a total lack of cooperation or abysmal record-keeping.
Hunt for Exceptions and Scope Limitations
After checking the opinion, your next stop is the section detailing the auditor’s tests and results. Here, you’re looking for exceptions. An exception is a documented instance where a control failed when the auditor tested it.
A few minor exceptions might be okay, especially if the vendor has a solid explanation and a plan to fix them. But a long list of exceptions—or repeated failures in critical areas like access control or change management—points to a weak security culture.
You also need to scrutinize the audit’s scope. Did the vendor conveniently leave a critical part of their service out of the audit? For example, if your team relies on their mobile app but the SOC 2 only covers their web platform, you’ve got a massive blind spot. A suspiciously narrow scope can be a clever way to hide weaknesses.
Understand Your Responsibilities with CUECs
One of the most overlooked parts of a SOC 2 report is the section on Complementary User Entity Controls (CUECs). These are the security tasks the vendor explicitly says are your job, not theirs.
Think of CUECs as the security instructions that come with a new product. If a vendor says, “You are responsible for enforcing strong user passwords,” and you don’t, then any breach from a weak password is on you—even if their SOC 2 report is perfect.
Ignoring these is a common and costly mistake. For a hands-on look at where these elements appear and how they are presented in a real-world document, you can review a SOC 2 report example here.
The business impact of getting this right is immense. With the average cost of a data breach hovering around $4.44 million, proper vendor due diligence isn’t just a checkbox item. It’s why buyers treat Type 2 reports as essential proof of a vendor’s commitment, with 96% of organizations in some studies citing it as the dominant standard for security assurance.
This decision tree shows how companies typically select the Trust Services Criteria that form the basis of their audit, starting with the mandatory Security criterion.
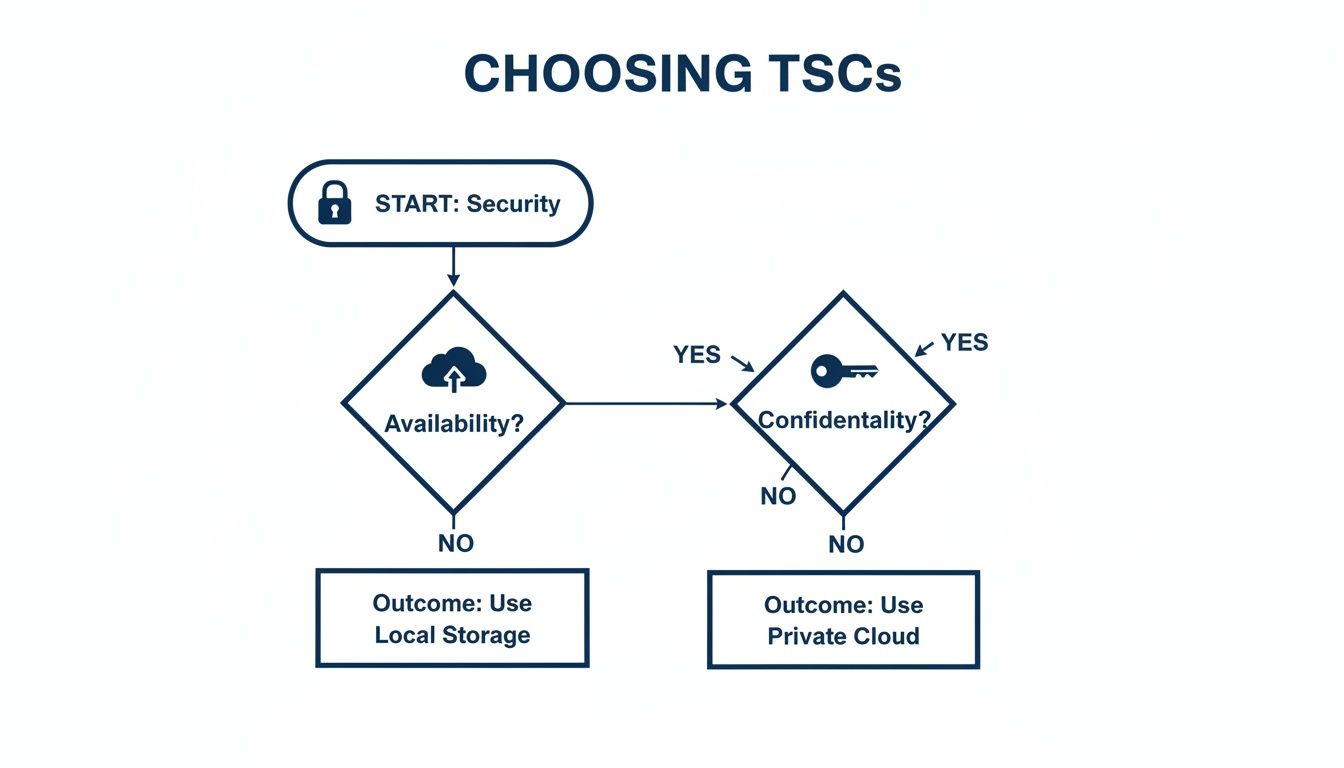
The flowchart makes it clear: after meeting the foundational Security requirements, a company’s choices for additional criteria like Availability or Confidentiality are driven entirely by the specific services they offer and the promises they make to their customers.
Planning Your Journey to a SOC 2 Type 2 Report
Getting a SOC 2 Type 2 report is a serious commitment, not a weekend project. The single most important thing you can do for a successful audit is to map out the entire journey—the timeline, the real costs, and the internal effort required. I’ve seen too many companies dive in without a clear plan, only to face painful delays and budget overruns.
This process is a marathon, not a sprint. It starts long before your auditor ever begins testing, with a critical readiness and remediation phase. This is where you roll up your sleeves, find the gaps in your controls, and implement the necessary fixes. This prep work alone can take several months of focused effort from your team.
Only after your controls are humming along does the clock start on the observation period. This is the 6 to 12-month window where your controls have to be working consistently for the auditor to test them. Rushing this step is a classic mistake that almost guarantees a qualified report or, worse, a failed audit.
Deconstructing the Timeline from Start to Finish
A realistic timeline for a first-time SOC 2 Type 2 report usually lands somewhere between 9 and 15 months. It’s a multi-stage process where each phase builds on the last. Don’t let anyone sell you on the idea that it can be done in a few weeks—that’s just not how a real Type 2 engagement works.
Here’s what the journey typically looks like:
- Readiness and Remediation (2-6 months): This is where you start with a gap analysis to see where you stand. Your team will spend this time writing policies, tweaking system configurations, and training staff to close those gaps.
- Observation Period (6-12 months): Once your controls are in place, the formal audit window opens. During this stretch, you have to live and breathe your new policies and gather the evidence that proves your controls are working day in and day out.
- Audit Fieldwork and Reporting (1-2 months): After the observation period closes, the auditor steps in to do their thing. They’ll request evidence, interview your team, and perform their tests before writing up their final report and official opinion.
Understanding the True Cost of an Audit
The cost of a SOC 2 report is much more than just the auditor’s invoice. While the audit fees themselves can range from $7,000 to over $100,000, the total investment is significantly higher when you add up all the pieces. For most small to mid-sized companies, the all-in cost—including readiness, tools, and internal time—is usually between $30,000 and $150,000. The global market for these services is projected to hit nearly $10.5 billion by 2030, which shows just how much demand there is for this level of security assurance.
Your budget has to account for more than just the final report. The real investment is in building a sustainable compliance program. That includes tooling, expert guidance, and your team’s most valuable resource: their time.
The most common “hidden” costs to watch out for are:
- Compliance Automation Tools: Platforms that help manage evidence collection and keep an eye on your controls. Expect to pay $5,000 to $15,000 a year for a subscription.
- Readiness Consultants: Bringing in an expert to guide you through the prep work can save a ton of time and prevent expensive mistakes down the road.
- Internal Staff Time: Getting ready for an audit often requires 100-200+ hours from your engineering and leadership teams. This is a major resource commitment that can’t be overlooked.
For a comprehensive breakdown of what to expect, check out our detailed guide on the SOC 2 Type 2 audit cost. Getting on the same page about time and money from the very beginning is the key to setting your company up for a smooth and successful audit.
Your Burning SOC 2 Questions, Answered
Even after you get the basics down, the finer points of a SOC 2 report can be tricky. Let’s tackle the most common questions we hear from companies navigating compliance for the first time.
How Long Is a SOC 2 Type 2 Report Good For?
A SOC 2 Type 2 report is generally considered valid for twelve months from the day it’s issued. Once it hits the one-year mark, it’s officially “stale,” and its power to assure prospects about your current security posture drops off a cliff.
This is why annual audits are the industry standard. Your customers, especially the big ones, want to see proof of an ongoing commitment to security—not a snapshot of what your controls looked like over a year ago. Consistent, yearly audits signal that your security program is a living, breathing process, not a one-time project.
What Happens If You Don’t Get a “Perfect Score”?
It’s a huge misconception that a SOC 2 audit is a simple pass/fail exam. The reality is far more nuanced. What you’re really after is an unqualified opinion from your auditor, which is the stamp of approval.
If an auditor finds significant issues with one or more of your controls, they might issue a qualified opinion. This means the report is mostly clean, but there are specific exceptions you—and your customers—will need to scrutinize. An adverse opinion is a major red flag indicating widespread control failures, while a disclaimer of opinion means the auditor couldn’t even get enough evidence to form a judgment.
How Is SOC 2 Different from ISO 27001?
While they’re both heavy hitters in information security, SOC 2 and ISO 27001 have fundamentally different philosophies and goals.
- SOC 2 is an attestation report, performed by a CPA firm, that digs into the nitty-gritty of your security controls against the AICPA’s Trust Services Criteria. It’s the go-to framework in North America for proving your controls are designed well and actually work over time.
- ISO 27001 is a certification. It validates that your organization has implemented a comprehensive Information Security Management System (ISMS). It’s more globally recognized and focuses on your overall risk management process rather than testing hundreds of individual controls.
Think of it this way: ISO 27001 certifies your system for managing security, while a SOC 2 Type 2 report attests to the actual performance of your security controls.
Does Every SaaS Company Need a SOC 2 Report?
Not every startup needs a SOC 2 report on day one. But it quickly becomes a non-negotiable ticket to play as you start selling to bigger customers. In the early days, you can probably get by with security questionnaires, but that strategy simply doesn’t scale.
The second you start targeting mid-market or enterprise clients, a SOC 2 Type 2 report transforms from a “nice-to-have” into a critical sales asset. These customers won’t gamble their data on a vendor without independent proof of security. For many, not having a report is an immediate deal-breaker, making it one of the most essential investments you can make for growth.
Finding the right auditor is the most critical step in your SOC 2 journey. At SOC2Auditors, we replace endless sales calls with a data-driven matching process. Get transparent pricing, timelines, and verified reviews to choose the perfect audit firm for your company with confidence. Find your ideal SOC 2 auditor at https://soc2auditors.org.