The Definitive Guide to SOC 2 Compliance Software

SOC 2 compliance software automates the grueling, manual process of preparing for a SOC 2 audit. Instead of chasing down screenshots and managing endless spreadsheets, these platforms plug directly into your tech stack to continuously pull evidence. This shifts compliance from a frantic, once-a-year fire drill to a proactive, automated part of daily operations.
For any company selling to enterprise customers, this transformation is critical. It’s how you prove your data protection isn’t just a policy—it’s a core, automated part of how you operate.
What Is SOC 2 Compliance Software
At its heart, SOC 2 compliance software is a purpose-built platform that automates the mapping of your internal controls to the AICPA’s five Trust Services Criteria. The Security criterion is mandatory, serving as the foundation. Organizations can then add optional criteria—Availability, Processing Integrity, Confidentiality, and Privacy—to create a flexible audit scope tailored to their specific services and risks, without relying on prescriptive checklists.
You can dig deeper into the basics in our complete guide on what is SOC 2 compliance.

Think of this software as your compliance command center. It integrates directly with your cloud infrastructure (e.g., AWS, Azure), HR systems, identity providers, and tools like GitHub or Jira. By tapping into these systems, it can automatically gather, format, and organize the proof your auditor needs to see.
From Manual Labor to Continuous Monitoring
In the past, preparing for SOC 2 was a nightmare of manual evidence collection. It meant hundreds of hours spent gathering screenshots, exporting logs, and tracking everything in massive spreadsheets—a process that was slow, tedious, and prone to human error.
SOC 2 compliance software automates this process by pulling real-time data, reducing manual screenshot gathering by 80-90% and minimizing human error. It transforms compliance from a reactive audit prep cycle into proactive risk management.
Instead of annual point-in-time checks, these platforms provide continuous monitoring that flags control failures or anomalies instantly. Whether it’s an unauthorized access attempt or a policy drift, the software alerts your team in real-time. This allows you to fix problems as they happen, preventing exceptions that could delay your report and shifting your posture from reactive to proactive.
Key Differences Between Audit Report Types
SOC 2 compliance software is built to support both types of audit reports. Understanding their distinct purposes is crucial for meeting customer expectations and unlocking larger deals.
| Report Type | Focus | Observation Period | Assurance Level |
|---|---|---|---|
| Type 1 | Evaluates the suitability of control design at a single moment. | Snapshot (as of a specific date) | Provides quick proof of intent; achievable in weeks. |
| Type 2 | Assesses the operating effectiveness of controls over time. | 6-12 months | Provides stronger assurance that controls consistently perform as intended, often a requirement for enterprise clients. |
How Automation Platforms Streamline Audits
SOC 2 compliance software is designed to plug directly into your company’s entire tech stack. Think of it as a central nervous system connecting to everything from your cloud infrastructure like AWS and Azure to your HR platforms, identity providers, and even development tools like Jira or GitHub. This deep, API-driven connectivity is what makes real automation possible.
Once connected, the software starts pulling real-time data to automatically gather audit evidence. It collects logs, verifies policy configurations, tracks access reviews, and grabs all the other critical proof your auditor needs, without anyone having to take a single screenshot. This process alone can slash the manual evidence-gathering workload by a staggering 80-90%.
Continuous Monitoring for Proactive Compliance
One of the most powerful features of these platforms is continuous monitoring. Instead of finding out about control failures during the annual audit scramble, you get instant alerts the moment something goes wrong. This flips compliance from a reactive, painful exercise into proactive, day-to-day risk management.
For instance, the system will immediately flag critical issues like:
- An employee receiving excessive permissions in a production environment.
- A key security setting drifting away from its required configuration.
- An access review that’s now overdue.
This real-time feedback loop lets your team fix problems as they happen, ensuring your controls are actually working throughout the entire audit period. It’s what prevents a minor slip-up from becoming a major exception that could derail your final SOC 2 report.
By turning compliance into an ongoing, automated activity, organizations maintain a constant state of audit readiness. This eliminates the last-minute fire drills and ensures that the evidence collected for a Type 2 report accurately reflects a strong, consistent security posture.
The Power of Extensive Integrations
The true value of any automation platform comes down to its integrations. Does it connect to the tools you actually use every day? The best platforms offer incredible technical breadth to cover a modern company’s diverse tech stack. It’s common to see top solutions offering anywhere from 80+ to over 375 integrations, which allows them to perform thousands of automated control checks across their global customer base.
This comprehensive connectivity is what turns abstract compliance rules into tangible, automated checks on your daily operations. Instead of manually proving a control is working, the software does it for you by constantly validating settings across your entire digital footprint. For help organizing which controls to track, you can use our detailed SOC 2 audit checklist. This approach doesn’t just make the audit easier—it fundamentally strengthens your company’s security.
Manual Audits Versus Automated Compliance
The old way of getting a SOC 2 report was a complete nightmare. It was a manual, soul-crushing marathon that had teams drowning in spreadsheets for months, desperately trying to collect evidence and take thousands of screenshots. It was slow, expensive, and a recipe for human error.
Today, SOC 2 compliance software offers a radically different path. It scraps that reactive, once-a-year fire drill and replaces it with a proactive, automated, and continuous process. This isn’t just about being ready for an audit; it’s about being secure all the time.
This change completely redefines what “audit-ready” even means. Instead of blocking out a huge chunk of time every year for audit prep, your company is always prepared. This is more than just a time-saver—it’s about building a fundamentally stronger, more trustworthy security program from the ground up.

A Direct Comparison
When you break down the actual tasks involved in a SOC 2 audit, the differences between the manual and automated approaches become crystal clear. Automation brings a level of efficiency and assurance that you simply can’t achieve with manual work alone.
To make it tangible, let’s look at a side-by-side comparison.
Manual Compliance vs SOC 2 Software A Direct Comparison
This table contrasts the traditional manual process for achieving SOC 2 compliance with the streamlined approach offered by automation software, highlighting differences in efficiency, cost, and overall effectiveness.
| Compliance Area | Manual Approach | Automated Software Approach |
|---|---|---|
| Evidence Collection | Endless manual screenshots and log exports; extremely high risk of human error and using outdated data. | Live API integrations pull real-time data directly from your systems, cutting manual work by 80-90%. |
| Control Monitoring | Point-in-time checks done once a year, leaving huge blind spots for the other 364 days. | Continuous, 24/7 monitoring that instantly flags control failures and policy drifts as they happen. |
| Audit Readiness | A reactive, high-stress scramble right before the audit, where you often discover big problems way too late. | An always-on, proactive stance where evidence is automatically collected and organized all year long. |
| Report Strength | Weaker evidence for Type 2 reports, which relies on a few samples to guess at effectiveness. | A strong, continuous evidence trail that proves control effectiveness over the entire observation period. |
| Strategic Value | Seen as a frustrating cost center and a necessary evil you have to endure to stay in business. | Becomes a strategic asset that builds real customer trust and helps close bigger deals, faster. |
The differences laid out here aren’t just minor improvements; they represent a fundamental change in how a company manages its security and compliance posture.
From Cost Center to Strategic Advantage
The traditional, manual approach makes compliance feel like a pure cost center. It’s a tedious, resource-draining chore you have to complete just to check a box. This cycle creates audit fatigue and a culture where security is seen as a roadblock, not a benefit.
SOC 2 compliance software flips this dynamic entirely. By embedding compliance into daily operations, it transforms a periodic burden into a continuous asset. The always-on audit readiness not only de-risks the audit itself but also becomes a powerful sales enablement tool, allowing teams to confidently demonstrate their security posture to prospects.
This shift is especially critical for SOC 2 Type 2 reports, which evaluate how well your controls worked over a 6-12 month period. Trying to manually prove that a control has operated flawlessly every single day for a year is nearly impossible. Automation, however, gives you a complete, timestamped log of evidence, offering auditors undeniable proof of sustained compliance.
This is the level of assurance that enterprise customers demand. In many cases, it becomes the key differentiator that unlocks larger, more valuable contracts and significantly shortens your sales cycles.
More Than Just an Audit: The Strategic Value of SOC 2 Software
Investing in SOC 2 compliance software isn’t just about passing your next audit. It’s about turning a yearly fire drill into a real strategic advantage. One of the biggest wins is consolidating your GRC efforts across multiple security frameworks.
Most companies don’t just stop at SOC 2. You might have customers asking for ISO 27001 or needing to comply with HIPAA. Since there is often up to 80% overlap between these standards, multi-framework support allows you to reuse SOC 2 evidence and controls. This can cut redundant documentation by 40-60%, positioning compliance as a scalable investment rather than a siloed annual burden.
Stop Ignoring Your Supply Chain Risk
Your security is only as strong as your weakest link, and a third-party vendor is often a common audit pain point. One slip-up from a partner can invalidate your own controls and expose you to cascading compliance failures.
Modern SOC 2 platforms tackle this head-on with built-in vendor risk management modules. These tools automate the most painful parts of securing your supply chain by:
- Automating Assessments: Sending, tracking, and managing security questionnaires without manual follow-up.
- Ongoing Monitoring: Getting continuous updates on a vendor’s security posture.
- Risk Scoring: Assigning clear risk scores to every vendor so you can focus your energy where it matters most.
This gives your auditor concrete proof that you have a serious third-party risk program in place.
From Cost Center to Revenue Engine
Executive dashboards provide quantifiable metrics on compliance health, incident trends, and ROI, transforming the conversation around compliance. You can finally draw a straight line from security efforts to business growth.
By providing metrics like reduced audit costs or faster sales cycles via trust centers, these dashboards transform SOC 2 from a cost center into a strategic asset that directly correlates with revenue growth and risk reduction.
This shift is critical, especially now that SOC 2 is a baseline requirement for most B2B deals. A 2025 industry report highlighted that 92% of organizations now perform two or more audits a year, with 58% conducting four or more. This isn’t just about checking a box anymore; the market demands continuous proof of your security. Explore more insights into evolving compliance statistics. This trend proves you need software that makes compliance an ongoing, value-driving part of your business, not just a once-a-year headache.
How to Choose the Right SOC 2 Compliance Platform
Picking the right SOC 2 compliance software is a make-or-break decision. It directly impacts whether you pass your audit, how much you spend, and your long-term security. The market is exploding to meet demand—the SOC 2 compliance automation space was valued at USD 1.45 billion in 2024 and is expected to grow by 16.8% annually. You can read the full research on this market growth if you want the deep dive.
To cut through the noise, start with integrations. Your platform must connect seamlessly with your cloud provider (AWS, Azure, GCP), identity provider (Okta, Google Workspace), HR system (Rippling, Gusto), and developer tools. If it has weak integrations, you’ll be right back to the spreadsheet hell you’re trying to escape.
Evaluating Automation Depth and Expert Support
Not all “automation” is the same. True automation means continuous monitoring that pulls real-time data, flags control failures instantly, and packages evidence for your auditor. Some platforms, however, also use AI to suggest control mappings, generate remediation guidance, and predict risks from patterns in system data, evolving compliance into an intelligent, adaptive process.
But even the best software can’t fully automate every task. The most valuable tools combine automation with access to compliance experts for bespoke guidance on scoping Trust Services Criteria and remediating gaps. This hybrid approach bridges the 20% of tasks, like nuanced risk judgments, that require human expertise.
The winning formula is simple: use technology for the repetitive 80% of compliance work and lean on human experts for the critical 20% that requires judgment. This combination is key to achieving 95%+ first-time audit success rates.
If you’re not sure what to expect from your auditor in the first place, our guide on SOC 2 auditor requirements is a good place to start.
Future-Proofing Your Compliance Investment
Your compliance needs are going to grow. Don’t just solve for today’s SOC 2 audit; pick a platform that sets you up for what’s next. Look for multi-framework support that lets you map your SOC 2 evidence to other standards like ISO 27001 or HIPAA.
This decision tree breaks down the real ROI of investing in compliance software versus sticking with manual processes.
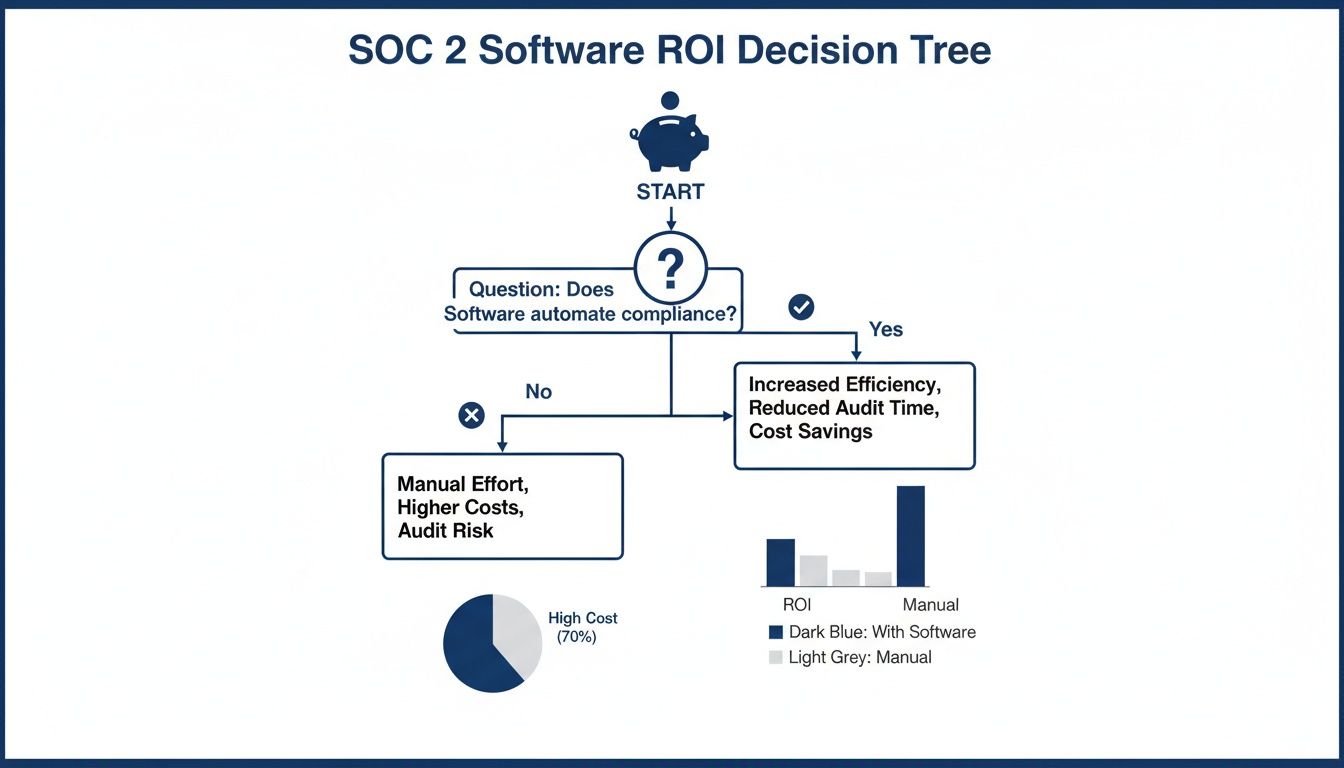
As the visual makes clear, automation is the smart path to value. Future-proof platforms are incorporating AI agents for evidence hunting, policy drafting, and questionnaire responses. This ensures sustained readiness amid evolving threats like AI governance risks, turning ongoing compliance into a competitive edge that builds enduring client trust beyond the initial report.
A Few Common Questions About SOC 2 Software
If you’re weighing the pros and cons of compliance software, you’re not alone. It’s a big decision. Here are some straight answers to the questions we hear most often, clearing up the confusion around timelines, report types, and where these tools actually fit in.
What’s the Difference Between a Type 1 and Type 2 Report?
This is easily the most common point of confusion. Getting this right is critical because it determines the entire scope and timeline of your audit.
A SOC 2 Type 1 report is a snapshot. It evaluates the suitability of control design at a single moment. It’s a faster way to get quick proof of your intent to be secure, and can often be achieved in weeks.
A SOC 2 Type 2 report, on the other hand, is a movie, not a snapshot. It assesses the operating effectiveness of your controls over a period of time—usually six to twelve months. This report provides stronger assurance to enterprise clients that your controls consistently perform as intended, often unlocking larger deals.
This is where SOC 2 compliance software really shines, especially for Type 2 audits. The continuous monitoring and automated evidence collection create a perfect, timestamped log proving your controls were working throughout the entire observation period. Trying to pull that together manually is a nightmare.
How Long Does It Take to Get Audit-Ready with Software?
One of the biggest selling points of SOC 2 automation software is speed. Every company’s situation is a bit different, but these platforms slash the prep time compared to using spreadsheets and elbow grease.
For a Type 1 report, many companies can get themselves audit-ready in just a few weeks. The software helps you knock out policies, map your controls, and pull together the initial evidence you need, fast.
For a Type 2 report, the prep work is similar, but then you have the mandatory observation period. The software starts collecting evidence from day one, so you can jump into that 6-12 month monitoring window almost immediately. As soon as that period ends, you have a clean, complete package of evidence ready for your auditor.
That speed isn’t just a nice-to-have; it means you can satisfy customer security demands faster and shorten your sales cycles.
Does This Software Replace My Human Auditor?
Let’s be crystal clear on this: no, SOC 2 compliance software does not replace your auditor. They play two completely separate—but equally important—roles.
Your auditor must be an independent, accredited CPA firm. Their job is to be the impartial third party who assesses your controls and issues the final SOC 2 report. They are strictly forbidden from helping you build or implement your compliance program because that would be a massive conflict of interest.
The software is your internal toolkit for preparation and management. It does the grunt work to get you ready for the audit by:
- Automatically collecting and organizing mountains of evidence.
- Continuously monitoring your controls and flagging failures in real-time.
- Making collaboration between your team and the auditor incredibly smooth.
Think of the software as your expert guide and automated assistant that builds the perfect, audit-ready case file. This lets the auditor do their job efficiently, which saves you a ton of time and dramatically lowers the risk of getting a qualified opinion or a report full of ugly exceptions.
Ready to stop dreading your next audit? SOC2Auditors helps you find the perfect, accredited audit firm for your business in minutes, not months. Get three tailored auditor matches today and streamline your path to compliance.