A Deep Dive Into SOC 2 Auditor Requirements for Compliance

Let’s get one thing straight from the start: not just anyone can perform a SOC 2 audit. The absolute, non-negotiable requirement is that your auditor must be an independent Certified Public Accountant (CPA) or a firm made up of licensed CPAs. This isn’t just a best practice; it’s a hard-and-fast rule from the American Institute of Certified Public Accountants (AICPA).
This rule exists for a simple reason: to guarantee the audit is objective, professional, and ultimately, trustworthy.
What Defines a SOC 2 Auditor

Think of a SOC 2 auditor as a professional inspector for your company’s digital house. A home inspector checks that the plumbing, electrical, and foundation meet strict building codes. In the same way, a SOC 2 auditor verifies your security controls against the AICPA’s Trust Services Criteria. Their job is to provide an unbiased, expert opinion on your security posture.
But this goes way beyond just checking boxes. Auditors are there to assess if your security systems are designed correctly (that’s a Type 1 audit) and, more importantly, if they actually work as intended over time to protect sensitive customer data (the all-important Type 2 audit). Their independence is the bedrock of the entire SOC 2 process, ensuring their final report is free from any internal company influence.
Core Qualifications and Responsibilities
In 2025, the core requirements for a SOC 2 auditor haven’t changed—they’re still centered on an independent assessment performed by an accredited CPA firm. These auditors dive deep into your organization’s internal controls to make sure their design is sound. For a Type 2 report, they go a step further, testing whether those controls have been operating effectively over a set timeframe, usually 3 to 6 months at a minimum. You can find more detail on the critical role of independent CPAs on trycomp.ai.
A legitimate auditor has a clear set of responsibilities. First, they need to truly understand the services you offer and the systems that power them. This isn’t just background noise; it’s the context they need to properly define the audit’s scope.
An auditor’s primary duty is not just to find faults. It’s to validate that you’re delivering on the security promises you make to your customers. Their independent opinion is the proof that bridges the trust gap between you and your clients.
Once the scope is set, their focus shifts to evaluating the controls you’ve put in place. This means detailed testing, sifting through evidence, and interviewing your team to confirm that your security measures are consistently practiced, not just written down in a policy document somewhere. The whole process culminates in the SOC 2 report, a powerful document that becomes a key sales tool and a symbol of trust for your business.
SOC 2 Auditor Key Responsibilities At a Glance
Getting a handle on an auditor’s responsibilities helps you prepare for the audit and work with them more effectively. The table below breaks down exactly what auditors are tasked with during a SOC 2 engagement.
| Auditor Responsibility | What This Means for Your Company | Primary Focus |
|---|---|---|
| Verify CPA Licensing | Only licensed CPAs from accredited firms can perform SOC 2 audits, guaranteeing professional standards are met. | Adherence to AICPA professional standards and ethics. |
| Maintain Independence | The auditor must be an unbiased third party with no conflicts of interest with your company. | Objectivity and integrity of the audit opinion. |
| Assess Control Design | For a Type 1 audit, the auditor evaluates if your controls are suitably designed to meet the chosen criteria. | Suitability and completeness of the control framework. |
| Test Operating Effectiveness | For a Type 2 audit, the auditor tests if your controls have actually worked consistently over a period of time. | Consistent application and real-world performance of controls. |
Knowing these core functions helps demystify the process. Your auditor isn’t an adversary; they are an independent validator tasked with verifying your security claims in a structured, professional manner.
What Evidence Auditors Will Ask For
Think of your SOC 2 audit as building a legal case for your security. Your policies are the claims you make, but auditors, just like judges, need concrete proof. They won’t just take your word for it.
You have to present compelling, objective evidence that your controls are actually working as designed, day in and day out. This is where the audit shifts from theory to reality. Auditors operate on a simple principle: trust but verify.
They will dig into a wide variety of documentation, logs, system configurations, and records to validate everything you claim. This evidence-gathering process is the absolute core of the audit. Without it, the final report is just an opinion. Learn more about the depth of SOC 2 evidence review at trycomp.ai.
Evidence for the Security Criterion
The Security criterion—often called the Common Criteria—is the foundation of every single SOC 2 audit. It’s mandatory. This principle is all about proving you protect information from unauthorized access, use, or disclosure.
To satisfy this, auditors need to see evidence of robust system protection. It’s not enough to say you have a firewall; you have to prove it’s configured correctly, monitored, and updated.
Here are some common examples of the proof they’ll demand:
- Access Control Lists: System-generated reports showing exactly who has access to which systems and data, along with the documented approvals for that access.
- Firewall and Router Configurations: Exported config files that show how you’re managing and restricting network traffic. No screenshots—they want the real files.
- Security Awareness Training Records: Signed attendance sheets or, more commonly, reports from your learning management system (LMS) proving employees completed their required security training.
- Vulnerability Scan Results: Reports from tools that scan your networks for weaknesses. Crucially, you’ll also need to show evidence of how you fixed any findings that came up.
Evidence for Availability and Processing Integrity
If you add Availability and Processing Integrity to your scope, the evidence requests get much more specific. Availability is about ensuring your systems are accessible and running as promised. Processing Integrity is about making sure data is handled completely, accurately, and on time.
For Availability, auditors are looking for proof of resilience. Can you take a punch and get back up quickly?
An auditor once told me, “A disaster recovery plan is just a theory until it’s tested.” The real evidence—the test results, the lessons learned, and the improvements you made—is what truly matters in an audit.
Common evidence for these criteria includes:
- Disaster Recovery (DR) Test Results: Detailed reports from your last DR test. They’ll want to see what was tested, the outcomes, and any issues you identified and fixed.
- System Uptime and Performance Reports: Dashboards and logs from your monitoring tools that demonstrate you are meeting your Service Level Agreements (SLAs).
- Data Backup Logs: System logs confirming that data backups are successfully completed according to your defined schedule, without errors.
- Quality Assurance (QA) Test Plans: Documentation showing how you test software changes before deploying them to production to ensure they don’t break things or corrupt data.
Evidence for Confidentiality and Privacy
Confidentiality and Privacy are often paired together, but they are distinct. Confidentiality is about protecting sensitive business data (like intellectual property or contracts), while Privacy is focused specifically on protecting personally identifiable information (PII).
For these criteria, the evidence centers on how you handle, encrypt, and dispose of sensitive data. Auditors need to see that you treat this information with the highest level of care throughout its entire lifecycle.
You’ll almost certainly be asked for the following:
- Data Encryption Policies and Configurations: Your documented encryption standards, plus screenshots of system settings proving data is encrypted both at rest (on disk) and in transit (over the network).
- Non-Disclosure Agreements (NDAs): Signed NDAs from employees, contractors, and key vendors who have access to confidential information.
- Data Disposal Records: Certificates of destruction or system logs that prove sensitive data was securely wiped when it was no longer needed.
- Privacy Policy and Consent Records: Your public-facing privacy policy and evidence showing how you obtain and manage user consent, especially if you’re subject to regulations like GDPR or CCPA.
Now, let’s break down how these evidence requests map to each of the five Trust Service Criteria. The table below provides a clearer picture of what auditors are looking for, policy by policy and control by control.
Sample Evidence Requirements by Trust Service Criterion
| Trust Service Criterion | Policy/Procedure Document Examples | Operational Evidence Examples |
|---|---|---|
| Security | - Access Control Policy - Information Security Policy - Incident Response Plan - Change Management Policy - Vendor Management Policy | - User access review reports (quarterly) - Firewall configuration files - Vulnerability scan reports (monthly) - Security awareness training completion records - Background check results for new hires |
| Availability | - Disaster Recovery (DR) Plan - Backup and Recovery Policy - System Monitoring Procedures - Service Level Agreement (SLA) documentation | - Annual DR test results and post-mortem - System uptime monitoring dashboards (e.g., from Datadog) - Backup completion logs (daily/weekly) - Capacity planning reports and meeting minutes |
| Processing Integrity | - Quality Assurance (QA) Testing Procedures - Data Input Validation Policy - Data Reconciliation Procedures | - QA test plans and results for recent code deployments - Error logs showing data validation failures and resolutions - Reports demonstrating reconciliation between systems - Change management tickets showing peer review and approval |
| Confidentiality | - Data Classification Policy - Confidentiality Policy - Data Handling and Disposal Procedures | - Screenshots of data encryption settings (at-rest and in-transit) - Signed Non-Disclosure Agreements (NDAs) from employees - Data loss prevention (DLP) tool alert logs - Certificates of data destruction |
| Privacy | - Privacy Policy (public-facing) - Data Subject Access Request (DSAR) Procedure - Data Retention Policy | - Records of user consent for data collection - Logs of completed DSARs (e.g., deletion requests) - Your company’s privacy notice or statement - Evidence of data destruction according to retention schedules |
Remember, this isn’t an exhaustive list, but it covers the most common requests you’ll encounter.
Ultimately, preparing and organizing this evidence is the most time-consuming part of any SOC 2 audit. Getting your documents and system outputs in order ahead of time is a critical part of meeting the SOC 2 auditor requirements and ensuring the whole process runs smoothly.
Navigating SOC 2 Timelines and Costs
Let’s get straight to it. The two questions on everyone’s mind when starting SOC 2 are: “How long is this going to take?” and “What’s the damage?”
While there’s no single price tag or timeline, you can absolutely get a realistic idea of what to expect. Knowing the typical phases and cost drivers is the key to planning a smooth audit without surprise bills or blown deadlines. Getting this right is critical to meeting the soc 2 auditor requirements.
Your SOC 2 journey isn’t a single sprint; it’s a multi-stage marathon. It kicks off with a Readiness Assessment to find your security gaps, followed by Remediation where you actually fix them. Only then does the formal Audit Period begin—the window of time your auditor observes and tests your controls.
This graphic lays out the entire process, showing you how everything fits together from day one to the final report.
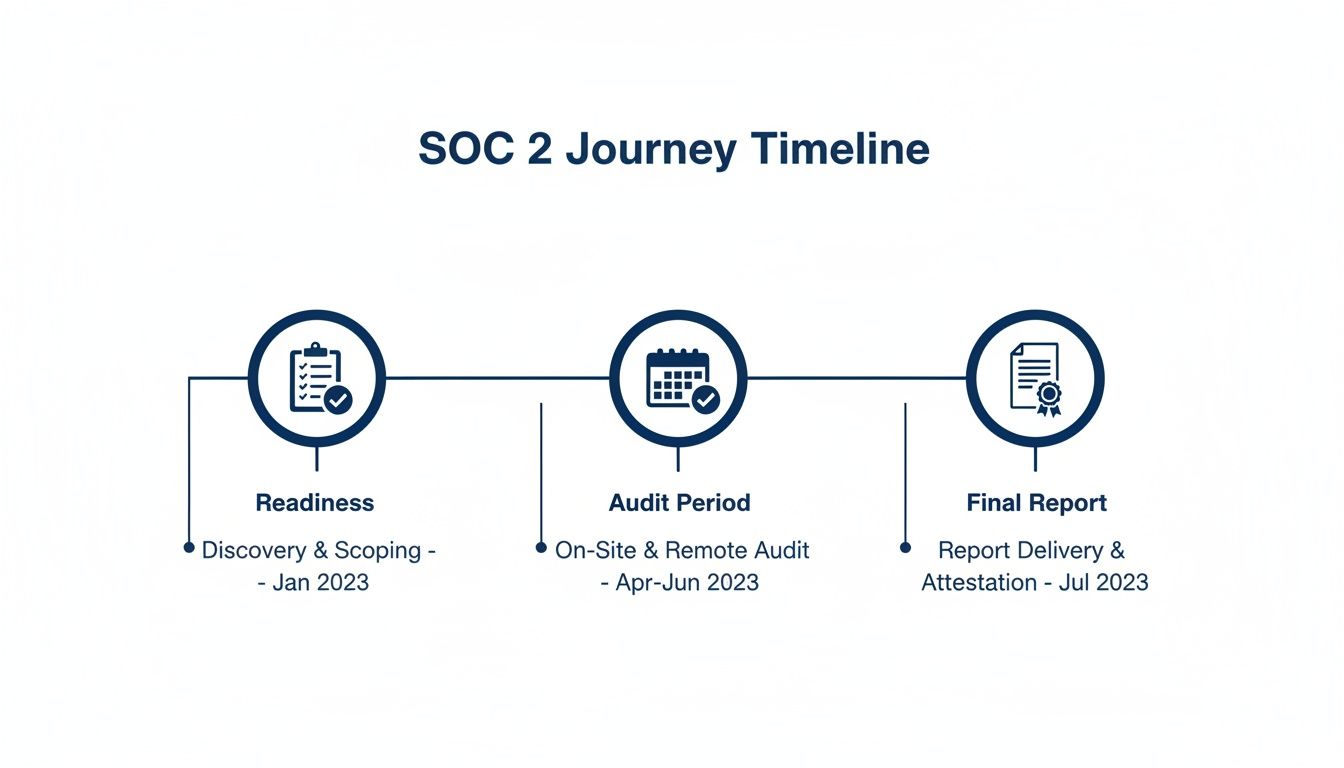
As you can see, the audit itself is just one piece of the puzzle. The real work happens upfront.
Understanding Audit Timelines
The biggest fork in the road for your timeline is whether you’re going for a Type 1 or a Type 2 report. The easiest way to think about it is a snapshot versus a movie.
A Type 1 report is a snapshot. It assesses the design of your controls at a single moment in time. Because there’s no long observation period, you can get this done in just a few weeks from the official audit start.
A Type 2 report is the full-length feature film. It evaluates if your controls are actually working effectively over a sustained period.
The core difference is proof over time. A Type 1 report shows you have a good plan on paper. A Type 2 report proves that your plan actually works day in and day out under real-world conditions, which is what most customers demand.
Type 2 audits require a continuous observation period, usually lasting anywhere from 3 to 12 months, to give the auditor enough evidence to sign off. It’s a much bigger commitment, but it’s also the report that enterprise customers almost always require.
Demystifying SOC 2 Costs
Just like timelines, costs can vary widely. There’s no standard price for a SOC 2 audit; the final number depends on a handful of key factors that dictate how much work your auditor needs to do.
Smart planning is your best friend here. Investing time and resources in the readiness phase can save you a fortune in rework and costly delays down the line.
Here are the main things that will move the needle on your audit bill:
- Company Size and Complexity: It’s simple, really. A 500-person company with a complex, multi-product infrastructure is a much bigger audit than a 20-person startup with a single SaaS app. More people, systems, and locations mean more work for the auditor.
- Audit Scope: The more Trust Services Criteria you add, the higher the cost. An audit for Security alone is the baseline. Each additional TSC—like Availability or Confidentiality—adds more controls to test, increasing the auditor’s workload and your final bill.
- Type of Report: A Type 2 audit is always more expensive than a Type 1. It involves a much longer period of testing, evidence gathering, and back-and-forth with the audit team.
- Auditor Reputation: You pay for the name. A “Big Four” accounting firm has the brand recognition but comes with a premium price tag. A smaller, specialized boutique firm can often deliver the same quality report for a fraction of the cost.
To get a much deeper dive into the numbers and what you should expect to pay, check out our complete guide on the factors that determine SOC 2 audit cost. It will help you build a realistic budget and make a smarter choice when you select your audit partner.
How to Select the Right SOC 2 Audit Firm
Picking a SOC 2 auditor isn’t just another vendor procurement task where you go with the lowest bidder. This is about choosing a long-term strategic partner. The right firm gives you more than a piece of paper—they offer genuine insights that make your security program stronger.
But the wrong one? That choice can lead to a frustrating, wildly expensive process that completely misses the point of the audit in the first place.
Think of it like hiring a specialist doctor for a critical check-up. You wouldn’t just pick a name out of a hat. You’d want someone with deep experience in your specific situation, a good bedside manner, and a reputation for being thorough. The exact same logic applies here. The quality of your audit experience almost always comes down to the partner you choose.
Evaluate Industry and Technical Expertise
Your first filter should always be experience. Does the audit firm actually understand your industry? An auditor who lives and breathes FinTech will grasp the nuances of financial data flows far better than one who mostly works with manufacturing companies. That specific industry knowledge means they’ll ask smarter questions and give you much more relevant feedback.
Just as important is their fluency with your tech stack. If your entire world runs on AWS, your auditor better be an expert in AWS security configurations, IAM roles, and CloudTrail logging. An auditor who is unfamiliar with your environment is going to spend a lot of your time (and your money) just trying to get up to speed.
To figure this out, you have to ask direct questions:
- “How many companies in the SaaS/HealthTech/FinTech industry have you audited in the past year?”
- “What’s your team’s real-world experience with AWS, Azure, or Google Cloud Platform?”
- “Can you walk me through how you audit controls inside a modern CI/CD pipeline?”
Assess Audit Philosophy and Approach
Beyond the technical chops, you need to get a feel for the firm’s audit philosophy. Are they collaborative partners, or are they rigid inspectors just looking to ding you? Some auditors see their role as simply finding faults. Others work with you to understand the context of your business and provide practical guidance when small issues pop up.
You’re looking for a firm that is professional and independent, but also pragmatic. A good auditor knows that no company is perfect. They can tell the difference between a minor administrative slip-up and a significant security flaw. That distinction is absolutely critical for getting a report that is both fair and useful.
The best auditors act as a strategic asset. They maintain their independence while providing practical advice that helps you improve, ensuring your SOC 2 report reflects a robust and realistic security program, not an unachievable standard of perfection.
This is where asking sharp, scenario-based questions during your vetting process pays off. Understanding how a firm handles real-world situations will tell you everything you need to know about what it will be like to work with them.
Key Questions to Ask Potential Auditors
Before you sign any engagement letter, make sure you have a direct conversation with the lead auditor who will actually be handling your account. Their answers will reveal their approach, their expertise, and how well their style fits your company’s culture.
Here’s a checklist of critical questions to guide that conversation:
- Support and Communication: What level of support should our team expect during the evidence-gathering phase? Who will be our main point of contact, and how responsive are they?
- Handling Exceptions: How do you handle minor control exceptions or deviations? Can you give me a specific example of how you’ve dealt with one in a past audit?
- Team Experience: What are the qualifications and experience levels of the actual team members who will be assigned to our audit? Are they senior-level, or will we be working with junior staff?
- Reporting Process: What does your reporting process look like from start to finish? What’s the typical turnaround time from the end of the audit period to us having the final report in hand?
Finding the right fit is a critical step in meeting the broader soc 2 auditor requirements for a successful engagement. For a deeper look into the selection process, our comprehensive guide on how to choose a SOC 2 auditor offers even more detailed criteria and tips.
Your Pre-Audit Readiness Checklist

A successful SOC 2 audit starts long before your auditor ever walks through the door (or logs into Zoom). Getting prepared isn’t just a nice-to-have; it’s the single biggest factor in having a smooth, predictable, and successful engagement.
Think of it like getting your house ready for a professional inspection before you sell it. You wouldn’t just cross your fingers and hope the inspector doesn’t find a leaky pipe. You’d do a walkthrough yourself, check the plumbing and electrical, and fix any problems ahead of time. This checklist is your pre-inspection walkthrough, making sure you’ve handled the soc 2 auditor requirements before the real audit begins.
Define Your Audit Scope
First things first: you can’t prepare if you don’t know what you’re preparing for. Defining your audit scope is the bedrock of the entire process.
This means deciding which of the five Trust Services Criteria (TSCs) actually apply to the promises you make to customers. Security is always mandatory. But do you also need Availability, Processing Integrity, Confidentiality, or Privacy?
Beyond the TSCs, you need to draw a clear line around the specific systems, services, people, and even physical locations that are in-scope. A fuzzy scope is a classic mistake that leads to auditing irrelevant systems or, even worse, completely missing critical ones that could cause a finding.
Conduct a Gap Analysis
With your scope locked in, it’s time for a gap analysis, often called a readiness assessment. This is essentially a dress rehearsal for the main event. You’ll compare your current controls against the specific criteria you’ve chosen and hunt for any weaknesses or gaps before your auditor does.
It’s a step that pays dividends. According to the Association of Certified Fraud Examiners (ACFE), companies that thoroughly prepare for compliance audits see a 40% higher success rate on their first attempt. That preparation almost always includes a readiness assessment to find and fix problems proactively.
A gap analysis transforms the audit from a test you’re hoping to pass into a simple validation exercise. You’re no longer guessing; you’re just proving you’ve already done the work.
This is such a crucial step that many companies bring in outside help to get it right. You can learn more about this process in our guide to a formal SOC 2 readiness assessment.
Assemble Your Team and Document Everything
Compliance is a team sport, not a solo mission. Start by designating one person to own the audit process. Then, identify the key players from other departments like engineering, HR, and legal who will need to be involved. Everyone needs to be on the same page about their role and why this audit matters.
Next, shift your focus to documentation. Your auditor will live by a simple rule: if it isn’t written down, it didn’t happen. From high-level security policies to the nitty-gritty of your operational procedures, everything needs to be documented.
Finally, you can start gathering the actual evidence. This is where the real work begins. Collect all the documents, logs, and reports your auditor will need and organize them in one central, secure place. A well-organized evidence library is a sign of professionalism that makes the entire audit faster and less painful for everyone involved.
Common Audit Pitfalls and How to Avoid Them
Learning from someone else’s mistakes is a lot cheaper than making them yourself. The SOC 2 audit process is a minefield of common traps that can easily derail even a well-intentioned company, leading to painful delays and surprise invoices. Knowing what these are is the first step to sidestepping them entirely.
One of the biggest blunders is poor scope definition. This goes wrong in two ways: either the scope is way too broad, pulling in irrelevant systems and creating a mountain of extra work, or it’s too narrow, completely missing the critical components that your customers actually care about. A good auditor will sniff out a sloppy scope from a mile away, forcing a costly and frustrating reset on the whole project.
Another classic mistake is treating compliance like a final exam you can cram for. The companies that sprint to the finish line and then immediately let their controls slide are setting themselves up for a painful follow-up audit. Auditors are paid to look for consistency, and a “set it and forget it” attitude is a massive red flag.
Where Audits Really Go Sideways: Evidence and Buy-In
If there’s one pitfall that will sink your audit, it’s failing to produce solid, high-quality evidence. It’s not enough to say you conduct quarterly access reviews; you have to show the tickets, the logs, the sign-offs, and the proof that you actually did it.
Without tangible evidence, a control simply doesn’t exist in the eyes of an auditor.
This problem is usually a symptom of a much deeper issue: a lack of buy-in from the rest of the company. If your engineering and IT teams see the audit as just another bureaucratic checklist, they won’t bother with the meticulous record-keeping that’s required. This forces the compliance lead to constantly chase people down and almost guarantees you’ll have gaps in your evidence.
An audit isn’t a test of your policies; it’s a test of your execution. The most beautifully written security policy is worthless without consistent, verifiable proof that it’s being followed every single day.
This is why the readiness phase has such a high return on investment (ROI). Spending time upfront to get your house in order dramatically reduces the risk of failure and expensive rework later. This is also where automated compliance platforms and AI-driven evidence validation tools can be a game-changer. You can find more strategies for accelerating SOC 2 readiness on dsalta.com.
How to Get Ahead of the Problems
Avoiding these headaches really comes down to planning ahead and changing your mindset. Stop thinking of compliance as a one-off project and start treating it as a normal part of how you operate.
- Host a Scoping Workshop: Get leaders from engineering, product, and HR in a room. Hammer out a precise audit scope and get everyone to agree on it. Document every system, data type, person, and location that’s in-bounds.
- Automate Evidence Collection: Don’t rely on humans to take screenshots. Use tools to automatically pull logs, capture configuration settings, and document changes. It saves your team from mind-numbing manual work and keeps your evidence clean and consistent.
- Communicate the “Why”: Don’t just tell people what to do; explain why it matters. Constantly remind the whole company that SOC 2 is critical for winning and keeping the customers that pay all our salaries. When people understand the business impact, they become allies instead of obstacles.
Common Questions We Hear During SOC 2 Audits
Even with the best preparation, a few practical questions always pop up during the audit. These are the real-world scenarios that aren’t always in the textbooks but are critical for keeping your SOC 2 process on track.
Let’s clear up some of the most common ones.
Can We Change Controls During the Audit Period?
Yes, but you need to be surgical about it and keep your auditor in the loop. Businesses change, and sometimes a control just isn’t working or needs an upgrade. This is especially common during a longer Type 2 observation period.
When this happens, you have to tell your auditor immediately. They’ll adjust their testing plan to cover the old control for the time it was active and the new one for the rest of the period. Documentation is your best friend here—you need a crystal-clear paper trail explaining why the change was made and the exact date it happened. This prevents any nasty surprises in the final report.
What Happens If the Auditor Finds an Exception?
First, don’t panic. An exception is not an automatic failure. It just means the auditor found a moment where a control didn’t operate exactly as you described it. Honestly, it happens more often than you’d think, and how you respond is what really counts.
The auditor will first figure out how often it happened and what the real-world impact was on your security. Then, your management team has to provide a formal response explaining the root cause and, more importantly, what you’ve done to fix it so it won’t happen again.
Think of an audit exception as a learning opportunity, not a scarlet letter. A transparent, well-documented management response actually shows you have a mature security program that can find and fix its own weaknesses. It can paradoxically make your report look stronger.
This whole back-and-forth—the finding and your response—gets included in the final report. A few minor exceptions are perfectly normal and acceptable to your customers. A lot of them, or a few really big ones, could lead to a “qualified opinion,” which is a much bigger deal.
Do We Need a SOC 2 Audit Every Year?
Yes, you absolutely do. Plan on making this an annual event. A SOC 2 report is really only considered valid by customers for about 12 months. The security world moves too fast for an old report to provide any real assurance.
This annual cycle reinforces that SOC 2 isn’t a one-time project to be checked off a list; it’s a continuous program. To keep the trust of your enterprise clients and meet your contractual promises, you have to gear up for a SOC 2 audit every single year.
Finding the right audit firm is the most critical decision in your SOC 2 journey. SOC2Auditors helps you compare 90+ verified firms based on real pricing, timelines, and industry experience. Get three data-driven matches in 24 hours and choose your auditor with complete confidence. Find your perfect SOC 2 auditor today.