Your Guide to the Complete SOC 2 Audit Timeline

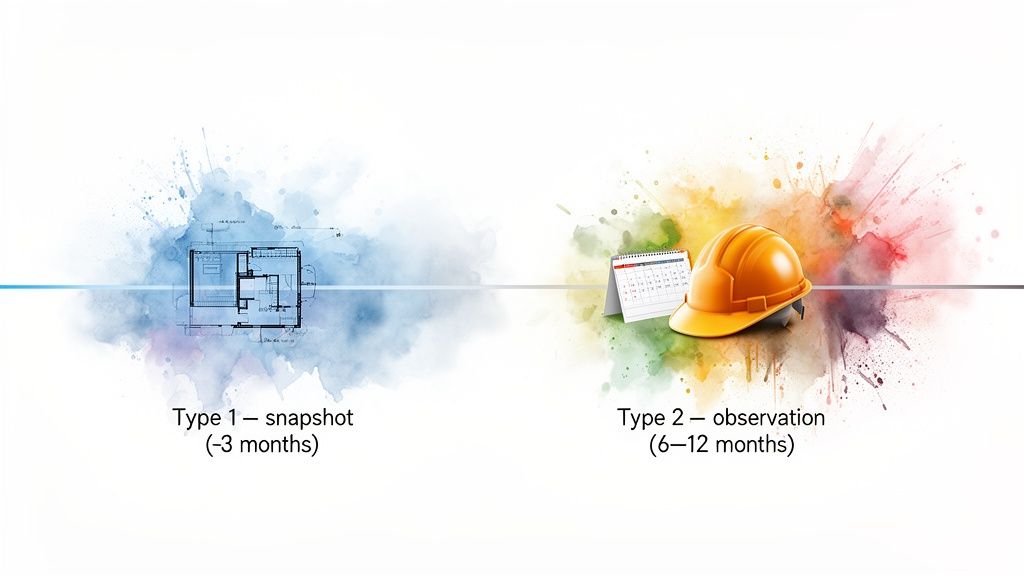
A SOC 2 audit can take anywhere from three months to over a year. The final timeline really boils down to two things: how mature your security program is today and which type of report you’re going for. A Type 1 audit is just a snapshot in time, but a Type 2 report observes your controls over a period of 3-12 months, which gives your customers much deeper assurance.
How Long Does a SOC 2 Audit Really Take?
Getting into a SOC 2 audit can feel like planning a major home renovation. You know the end goal—a secure, trustworthy system—is non-negotiable, but the path to get there seems overwhelming. There’s no single answer for how long it takes; it’s all about your starting point and your destination.
Think of the two report types like this:
- SOC 2 Type 1: This is like having an architect review your blueprints. An auditor inspects your security controls at a single moment to confirm they are designed correctly. It’s the faster option and provides a solid baseline of assurance.
- SOC 2 Type 2: This is the full, multi-month inspection of the finished house. The auditor observes your controls in action over an extended period (usually 6-12 months) to verify they are operating effectively day in and day out.
This timeline breaks down the core phases every SOC 2 journey follows, from the initial prep work to getting the final report in your hands.
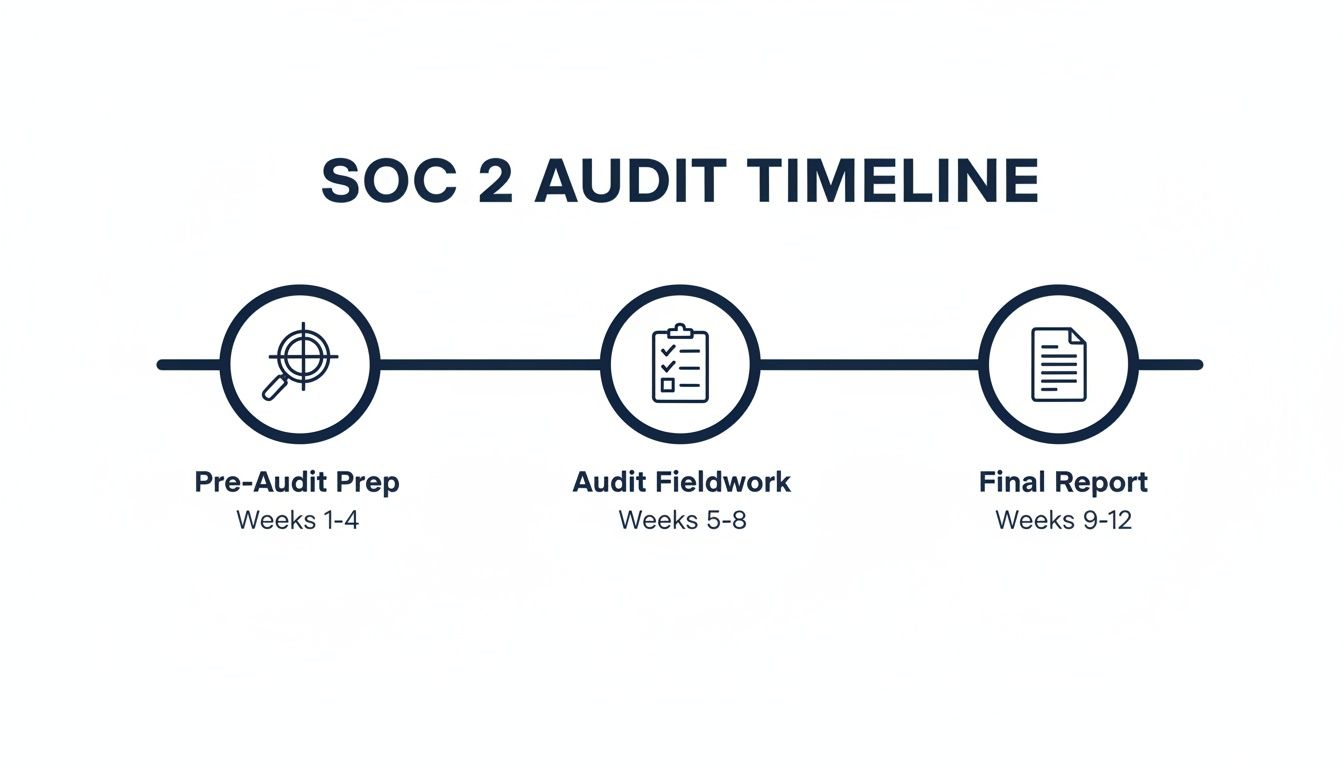
As you can see, the real heavy lifting happens in the pre-audit phase. Nailing your preparation is the single biggest factor in how quickly and smoothly the rest of the audit goes.
To give you a clearer picture, let’s look at how the timeline differs for each report type.
SOC 2 Audit Timeline At a Glance: Type 1 vs. Type 2
This table offers a quick comparison of the time commitment for the main stages of both a Type 1 and Type 2 audit.
| Audit Stage | Typical Type 1 Timeline | Typical Type 2 Timeline |
|---|---|---|
| Readiness & Remediation | 1-3 months | 2-4 months |
| Observation Period | Not Applicable | 3-12 months |
| Audit Fieldwork & Testing | 2-5 weeks | 3-6 weeks |
| Final Report Delivery | 2-4 weeks | 3-5 weeks |
| Total Estimated Time | 3-6 months | 9-18 months |
The standout difference, of course, is the observation period, which is the heart of a Type 2 audit and the primary reason for its longer duration.
The Initial Sprint for a Type 1 Report
For many startups aiming for their first SOC 2 Type 1, the process is often more manageable than they expect, usually wrapping up in just 3 to 6 months. This breaks down into two key phases: a 1-3 month pre-audit period for scoping and gap analysis, followed by a 2-5 week official audit where the CPA firm digs in. You can see how experts at compliance platforms like Scrut map this out.
A common misconception is that the audit itself is the longest part. In reality, the readiness and preparation phase is where you have the most control. A thorough readiness assessment can turn a chaotic, year-long slog into a focused, three-month project.
Extending the Journey for a Type 2 Report
A SOC 2 Type 2 audit includes every step of a Type 1 but adds the critical “observation period.” This isn’t an active audit phase; it’s a monitoring window where your controls must consistently work as designed.
This period is the main reason a Type 2 timeline stretches out, often taking 9 to 18 months from start to finish. While the actual audit fieldwork might still only take a few weeks, the evidence has to be collected from across this entire window, proving your controls are effective over the long haul.
Building Your Foundation with Readiness and Scoping
Don’t mistake this first stage for preliminary paperwork. The readiness and scoping phase is the single most critical factor in determining how fast—and how successfully—your entire SOC 2 audit unfolds.
Think of it like a chef’s mise en place. It’s the painstaking prep work of chopping vegetables and measuring spices before the heat is even turned on. Nailing this part means identifying and fixing control weaknesses early, saving you from a world of expensive delays down the line. Get this right, and you turn a painful chore into a serious strategic advantage.
Selecting Your Trust Services Criteria
Your first big decision is choosing which Trust Services Criteria (TSCs) to include in the audit. Security (often called the Common Criteria) is the mandatory foundation for every single SOC 2 report. No exceptions.
The other four—Availability, Processing Integrity, Confidentiality, and Privacy—are optional. Your choices here should be guided by one thing: what you promise your customers. For instance, a cloud storage provider that guarantees uptime absolutely needs to include Availability. A platform handling sensitive healthcare data would be foolish to skip Confidentiality and Privacy.
- Security: The non-negotiable bedrock of every SOC 2.
- Availability: Proves your systems are up and running as advertised.
- Processing Integrity: Confirms your system does what it’s supposed to—accurately and completely.
- Confidentiality: Covers how you protect sensitive data from being seen by the wrong people.
- Privacy: Addresses how you collect, use, and get rid of personal information.
Picking the right TSCs is a balancing act. Aim too low, and you won’t satisfy enterprise clients. Aim too high, and you’ll needlessly drag out your timeline and inflate your costs.
Defining a Clear and Defensible Audit Scope
Once you’ve locked in your TSCs, it’s time to draw the boundaries of your audit. This is where you define exactly which systems, services, people, and infrastructure are “in-scope” for delivering on the promises you made with your TSC selection.
A poorly defined scope is one of the top reasons for audit delays. Scope creep—where the goalposts move mid-audit—can tack on weeks or even months to your timeline and lead to a nasty surprise on your final invoice.
Work with your team to document every single component that will be audited. Be specific. List the applications, databases, physical locations, and even the third-party vendors that support your service. Getting this right from day one ensures your team and your auditor are reading from the same playbook.
Executing a Thorough Gap Analysis
A gap analysis, also known as a readiness assessment, is your audit dress rehearsal. It’s your chance to find and fix all the ugly stuff before an auditor ever lays eyes on it. The process is simple: compare your current security controls against the requirements of the TSCs you chose.
This process will shine a spotlight on any “gaps” where your practices fall short of SOC 2 standards. Maybe you’ll find out your employee offboarding process is just a verbal reminder, or that you haven’t actually tested your data backup procedures in a year.
A key part of building your foundation is knowing how to document your controls properly. For a deep dive, check out this guide on mastering a standard operating procedure template to get your documentation in order. This isn’t just audit prep; it’s just good security hygiene.
Closing these gaps is where the real work happens. This could mean writing new policies, rolling out new security tools, or training your team on updated processes. If you need a roadmap, our detailed https://soc2auditors.org/insights/soc-2-readiness-assessment-checklist/ can make sure you don’t miss a thing. Seriously, taking the time to remediate gaps is the most effective thing you can do to shorten your overall SOC 2 audit timeline.
Navigating Audit Fieldwork and Evidence Collection

This is where the rubber meets the road. The fieldwork and evidence collection phase turns all that theoretical prep work into a real, live audit. Think of it as the open-book exam of your compliance journey.
If you nailed the readiness phase, this stage feels like a smooth, structured verification process. If not, it can quickly devolve into a frantic scramble that blows up your timeline. Forget the old-school image of auditors locked in a conference room for weeks. Modern fieldwork is a dynamic, back-and-forth process of testing and validation where your policies meet reality.
What Auditors Are Really Looking For
Auditors don’t just take your word for it; they need proof. They use a few core methods to test your controls, each designed to gather a different type of evidence. Knowing what they’re after helps you prepare the exact proof they need, which is the secret to keeping your SOC 2 audit timeline on track.
They’ll primarily use a mix of three techniques:
- Inquiry: This is just a fancy word for interviews. Auditors will talk to your team—asking your sysadmins about server configurations or your HR manager about the new hire onboarding process.
- Observation: Here, auditors watch a process as it happens. They might sit in (virtually, of course) as a developer deploys code to production, just to see if your change management controls are being followed.
- Inspection: This means reviewing documents and records. Auditors will dig through system logs, policy documents, vendor contracts, and meeting minutes to find hard evidence that your controls are actually working.
A strong evidence package combines all three. For example, to test your quarterly user access review control, an auditor might interview the manager responsible, observe them performing the review, and then inspect the signed-off report from last quarter.
Streamlining Your Evidence Collection Process
The evidence collection part can feel like a firehose of requests, with auditors sometimes asking for hundreds of individual items. A disorganized approach here is a one-way ticket to delays. The key is a centralized system and clear ownership for every single request.
The fieldwork phase—where auditors conduct walkthroughs of your environment—can realistically take anywhere from 2 to 6 weeks. However, as experts who have completed over 5,000 assessments note, fitting this into a minimum 8-week total audit window shows just how easily timelines can expand without proper preparation.
This phase involves deep dives into the people, tech, and processes tied to your chosen Trust Services Criteria. The timeline scales up or down based on the number of locations, applications, and criteria in scope. Adding criteria like Availability or Confidentiality can easily increase the complexity and time required by up to 50%.
To keep things moving, create a master evidence request list (your auditor will provide one) and assign a specific owner from your team to each item. That person is on the hook for gathering the right documentation, screenshots, or logs and getting them to the auditors.
From Screenshots to System Descriptions
While a ton of the evidence will be tangible things like configuration screenshots and policy documents, you’re also responsible for writing a crucial narrative called the system description.
This document is the story of your control environment. It explains what your company does, what services are in scope for the audit, and the infrastructure, software, and people that support them. It provides context for the auditors and, eventually, for the clients who will read your final SOC 2 report. It’s your chance to showcase the maturity of your security program, so it should be written with care.
A big part of this is properly documenting the controls themselves; you can learn more about building an effective internal control procedure in our detailed guide.
By organizing your evidence, prepping your team for interviews, and drafting a clear system description, you can make the fieldwork phase a testament to your preparation. This proactive approach not only keeps your audit on track but also builds a strong, trusting relationship with your audit firm.
Understanding the Type 2 Observation Period

The observation period is what gives a SOC 2 Type 2 report its teeth, but it’s easily the most misunderstood part of the timeline. Let’s be clear: this isn’t a phase where auditors are constantly breathing down your neck.
Instead, think of it as a probationary period for your security program. You’ve designed the controls, put them in place, and now you have to prove they actually work, day in and day out, over an extended period. This window typically lasts between six and twelve months, though some first-timers opt for a shorter three-month sprint.
The Role and Purpose of the Observation Period
The whole point of this period is to gather evidence of operating effectiveness. A Type 1 report is like a blueprint—it shows you have a good design on a single day. A Type 2 is like a time-lapse video of that building withstanding storms for a year, proving its resilience.
Auditors will sample evidence from across the entire observation window. They don’t just ask if you have a security training policy for new hires. They’ll pull the records for employees who started in January, April, and September to verify each one completed the training on time, just like your policy says.
The length of your observation period sends a direct message to your customers about the maturity of your security posture. A longer period, such as twelve months, provides a higher level of assurance and is often preferred by enterprise clients.
This is what makes the Type 2 report the gold standard. It demonstrates a sustained commitment to security, not just a scramble to pass an audit. For a deeper dive, our guide explains in detail what is a SOC 2 Type 2 report and why it carries so much weight.
Can You Shorten the Observation Period
Yes, but it’s a trade-off. The most common reason to go with a shorter period is a big deal on the line that requires a report, fast.
- Standard Period: 6-12 months is the industry norm and what enterprise customers expect to see. It provides the strongest assurance.
- Minimum Period: 3 months is generally the shortest an auditor will accept for a first-time Type 2 report.
- Subsequent Reports: After your first audit, you’ll almost always move to a 12-month observation period to provide continuous coverage year after year.
A three-month report can get you over the finish line, but be aware that some savvy enterprise customers might view it as less comprehensive. It’s a strategic call, balancing the need for speed against the level of assurance you want to project.
What Happens When a Control Fails During this Period
First, don’t panic. Control failures, or exceptions as they’re called in the audit world, are pretty common, especially during your first go-around. An exception doesn’t automatically mean you’ve failed the audit.
Let’s say your policy requires quarterly access reviews, but the Q2 review was completed two weeks late because the main person responsible was on unexpected medical leave. That’s an exception. The key is how you respond when the auditor finds it.
Your response needs to be direct and professional:
- Acknowledge the Failure: Own it. “Yes, this control did not operate as designed.”
- Provide Context: Explain why it happened. The unexpected medical leave is a perfectly valid reason.
- Detail Remediation: Show you’ve fixed it and have a plan to prevent it from happening again. For example, you’ve now assigned a backup owner for all critical controls.
This entire exchange—the finding, the context, and your response—goes into the final report. A few well-managed exceptions can actually show transparency and a mature approach to continuous improvement. A report full of unaddressed failures, however, could lead to a “qualified” opinion, which is a major red flag for customers.
You’ve navigated the scoping, readiness, evidence collection, and fieldwork. The finish line is in sight. The last leg of the journey is turning all that hard work into a formal, signed SOC 2 report. This final stage typically takes four to seven weeks and officially wraps up the audit.
It all starts when your auditor disappears into their cave to analyze the mountain of evidence your team provided. Their job is to form an opinion on whether your controls actually meet the Trust Services Criteria you committed to. This isn’t just a simple thumbs-up or thumbs-down; it’s a detailed assessment that culminates in a draft report.
From Draft to Final Report
The first big moment in this final stretch is getting that draft SOC 2 report. Think of this as your last chance to review and correct the record before it’s set in stone. Your team needs to read every single section, paying razor-sharp attention to the system description, the auditor’s testing notes, and, most importantly, any exceptions they found.
This is your window to fix factual errors or add context where something might be misinterpreted. Once your team gives the green light, there’s one last, crucial legal step.
Management Assertion Letter Before they can issue the final report, your auditor will send you a management assertion letter to sign. This is a formal document where your company’s leadership swears that all the information provided was accurate and the system description is a fair representation of your environment. Signing this is a non-negotiable final step.
With the signed letter in hand, the auditor will issue the final, official SOC 2 report. It’s no longer a draft—it’s the asset you’ll use to build trust with customers and get deals done.
Understanding Your Audit Opinion
The absolute centerpiece of your SOC 2 report is the auditor’s opinion. This one statement summarizes the outcome of the entire audit and it’s the first thing your prospects will flip to. There are a few possible outcomes, and each one has huge implications for your business.
Here’s a simple breakdown of what each opinion really means:
- Unqualified Opinion: This is the gold standard. It’s a clean bill of health. It means the auditor found your controls are designed and operating effectively without any major issues. This is exactly what you’ve been working for.
- Qualified Opinion: This means the auditor found one or more significant problems, but the issues are isolated and don’t wreck the whole system. Think of it as a yellow flag for customers, pointing to a specific area of weakness they will absolutely ask you about.
- Adverse Opinion: This is the worst-case scenario. It means the auditor found widespread, material weaknesses. Your system, as a whole, does not meet the SOC 2 standards. An adverse opinion is a deal-killer.
- Disclaimer of Opinion: This is pretty rare. It happens when the auditor couldn’t get enough evidence to form any opinion at all. This might happen if a company put major limitations on the audit scope, preventing the auditor from doing their job.
Receiving your final report—hopefully with that unqualified opinion—marks the successful end of your SOC 2 audit timeline. But it’s way more than a certificate. It’s a powerful tool that proves your commitment to security and becomes a cornerstone of your sales and compliance strategy.
How to Avoid Common Delays in Your SOC 2 Timeline
Even the best-laid SOC 2 audit timeline can get knocked off course. Knowing the common roadblocks ahead of time is the single best way to keep your audit moving and on budget. These aren’t just little speed bumps; they can tack on weeks or even months of painful delays.
The biggest offender, without a doubt, is scope creep. This is what happens when you don’t nail down the audit’s boundaries from the start. New systems or controls get thrown into the mix halfway through, causing total chaos. It’s like planning a cross-country drive from New York to LA but suddenly deciding to detour to Miami—it wrecks the entire schedule.
Another huge delay comes from having unprepared teams. If the people who own the controls don’t actually understand what they’re responsible for or what evidence they need to pull, the audit grinds to a halt. This lack of readiness forces a last-minute scramble to produce sloppy evidence, which auditors will reject, starting the whole frustrating cycle over again.
Proactive Strategies to Prevent Delays
To protect your timeline, you have to get out of reactive mode. The best defense is a good offense, and that starts with a rock-solid audit scope that every stakeholder has signed off on before the audit even begins.
Create a formal scope charter that spells out every single system, application, and process that’s in play. This document becomes your North Star, preventing any of those tempting but disastrous detours.
You also have to assign clear ownership for every control. Don’t just wait for the auditor’s request list. As part of your readiness work, build a master list of controls and assign a primary and secondary owner to each. This guarantees someone is always on the hook for gathering the right evidence, even if a key person is out of office.
An audit exception is when you fail to follow your own documented policies. If an auditor flags a potential exception, dig into it immediately. Sometimes, a reasonable explanation is all they need to withdraw it, saving you from a reported finding and the follow-up delays that come with it.
Top 5 SOC 2 Delays and How to Prevent Them
Let’s be honest, things go wrong. But most SOC 2 delays are predictable and preventable. This table breaks down the usual suspects that derail audit timelines and gives you a simple, no-nonsense strategy to get ahead of each one.
| Common Delay | Impact on Timeline | Prevention Strategy |
|---|---|---|
| Scope Creep | Adds 2-4 weeks | Create a stakeholder-approved scope charter before the audit begins and enforce a strict change control process for any scope modifications. |
| Unprepared Teams | Adds 3-5 weeks | Assign control owners early and conduct internal training sessions to ensure everyone understands their responsibilities and evidence requirements. |
| Poor Evidence Quality | Adds 2-3 weeks | Validate all evidence against auditor requirements before submission. Use a compliance platform like Vanta or a centralized checklist to track quality. |
| Vendor Dependencies | Adds 1-4 weeks | Identify all critical third-party vendors in scope and request their compliance documents (e.g., their own SOC 2 report) well in advance. |
| Slow Auditor Response | Adds 1-2 weeks | Select an audit firm known for responsiveness. Establish clear communication channels and weekly check-in meetings from the start. |
When you treat your SOC 2 audit like any other mission-critical project—with clear goals, defined roles, and proactive planning—you can sidestep these common traps. It’s an approach that not only gets you a faster, smoother audit but also builds a stronger, more resilient security culture along the way.
Frequently Asked Questions About the SOC 2 Audit Timeline
Getting a SOC 2 report always brings up a ton of questions. Let’s tackle some of the most common ones so you can get a clearer picture of the road ahead.
Can We Shorten the SOC 2 Audit Timeline?
Yes, you can absolutely speed things up. The biggest leverage you have is in the readiness phase.
A sharp, focused readiness assessment can take months of painful prep work and condense it into just a few weeks. It’s all about finding and fixing the gaps before the auditor’s clock starts ticking. Using compliance automation software is another huge accelerator, as it eliminates most of the mind-numbing manual evidence collection.
For a Type 2 report, you can sometimes negotiate a shorter observation window—say, three months instead of the typical six—if you have a monster deal on the line. And finally, picking a responsive audit firm is critical. A team that answers emails the same day versus next week can make or break your schedule.
The fastest way to a successful audit is to invest heavily in preparation. A well-executed readiness assessment not only shortens the timeline but also significantly reduces the risk of audit exceptions and a qualified opinion.
How Does a Specialist Firm Compare to a Big Four Auditor?
Your choice of auditor has a massive impact on your SOC 2 audit timeline. Specialist or boutique firms are built for speed and agility. They often have faster scheduling, quicker turnaround times, and are a perfect fit for startups and mid-market companies where every week counts.
The Big Four firms, on the other hand, bring serious brand recognition, which can be a requirement for some enterprise customers. But that prestige comes with a tradeoff—more rigid processes and much longer lead times for scheduling. It really boils down to what you value most: the speed and focus of a specialist or the brand stamp of a Big Four firm.
How Does Company Size Affect the SOC 2 Timeline?
Company size and complexity are two of the biggest factors driving your timeline. Think of it this way: a small startup with a single, straightforward cloud product might be able to knock out a Type 1 audit in as little as three months.
Now, picture a large enterprise. They’ve got multiple products, a sprawling hybrid infrastructure, and hundreds of employees. Their audit scope is just fundamentally larger. That means more controls to test, mountains more evidence to gather, and way more people to interview. Each of these things adds significant time to every single phase of the audit.
If you’re just getting your head around the basics, this article on What Is SOC 2 Compliance is a great place to start.
Finding the right auditor is the most critical decision you’ll make in your SOC 2 journey. At SOC2Auditors, we replace the guesswork with a data-driven matching platform. Get transparent pricing, timeline benchmarks, and three tailored auditor matches in 24 hours to ensure your audit is fast, affordable, and successful. Find your perfect auditor at https://soc2auditors.org.