How to Become a SOC 2 Auditor A Complete Career Roadmap

So you want to become a SOC 2 auditor? It’s a smart move. This isn’t just another IT job; it’s a specialized career at the intersection of technology, business process, and security assurance. You’re the one who validates that a company’s promises about security are actually true.
Your Roadmap to a SOC 2 Auditor Career
Breaking into this field is a journey, not a sprint. It’s a deliberate path that builds on a specific mix of education, hands-on experience, and respected certifications. Think of it as climbing a ladder where each rung—from your first internal audit role to earning your Certified Information Systems Auditor (CISA)—prepares you for the next.
The demand right now is intense. By 2025, the market has exploded, with over 90 audit firms scrambling to serve thousands of tech companies. Why the boom? Because for most SaaS and cloud businesses, a SOC 2 report is the key that unlocks enterprise deals. Without it, they can’t get past security reviews.
Charting Your Path Forward
A clear strategy is non-negotiable. You need to map out your education, the exact experience you’ll chase, and a realistic certification timeline. This isn’t just about winging it; it’s about building a career curriculum tailored to this specific role. For some solid frameworks on how to structure this, check out these actionable employee development plan examples.
This timeline gives you a bird’s-eye view of the typical milestones most successful auditors hit along the way.
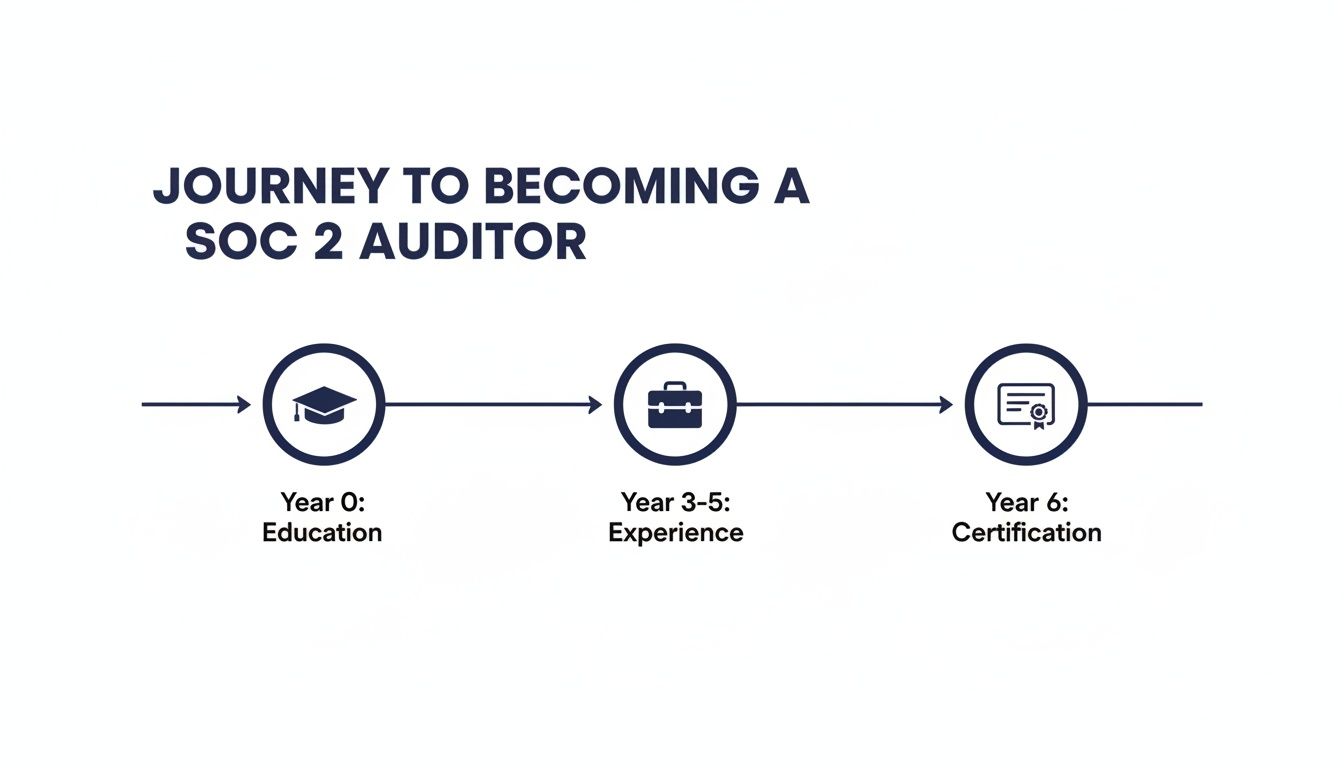
As you can see, each stage logically builds on the last. You start with the fundamentals, apply them in the real world, and then formalize that expertise with credentials that prove you know your stuff.
To give you a clearer picture, let’s break down what this journey looks like from start to finish. This table outlines the typical milestones, how long they usually take, and what you should be focusing on at each stage.
SOC 2 Auditor Career Milestones At a Glance
| Milestone | Typical Timeframe | Key Focus Areas & Certifications |
|---|---|---|
| Foundational Education | 4 Years | Bachelor’s in Accounting, IS, or Cybersecurity. Focus on core IT, audit, and business principles. |
| Entry-Level Experience | 1-3 Years | Roles in IT Audit, Internal Audit, or Risk Advisory. Master IT General Controls (ITGC) and control testing. |
| Key Certification (CISA) | 3-6 Months (Study) | The CISA (Certified Information Systems Auditor) is the gold standard. A CPA is also highly valued. |
| SOC 2 Specialization | 3-5+ Years | Move into a dedicated SOC 2 role. Lead engagements, mentor junior staff, and review complex systems. |
| Senior/Management Role | 5-8+ Years | Manage a portfolio of clients, lead practice development, and potentially earn the CISSP for deep security expertise. |
This isn’t a rigid timeline, but it’s a realistic one. Your mileage may vary, but hitting these milestones is what separates the candidates who get the offers from those who don’t.
The Three Pillars of Your Career
Your entire career roadmap balances on three core pillars. If one is weak, the whole structure can wobble.
- A Solid Academic Foundation: Most auditors start with a bachelor’s degree in accounting, information systems, cybersecurity, or a related field. This is where you learn the language of business processes, IT controls, and risk management. It’s the essential bedrock.
- Critical Certifications: This is non-negotiable. Credentials like the CISA or Certified Public Accountant (CPA) are the industry’s seal of approval. Top firms often won’t even look at a resume without them. They prove you’ve met a high standard of expertise.
- Irreplaceable Hands-On Experience: You can’t learn this job from a book. The real learning happens in the trenches—testing controls, interviewing engineers, and navigating tricky client situations. Roles in internal audit, IT audit, or risk advisory are where you cut your teeth and learn how theory applies in the messy real world.
This career isn’t about ticking boxes on a checklist. It’s about deep-diving into complex systems, understanding how risk flows through an organization, and communicating your findings in a way that helps companies build real, lasting trust with their customers.
Mastering the Core Competencies and Knowledge Base
To make it as a SOC 2 auditor, you need to go way beyond general IT theory. This job demands a specialized understanding of the frameworks that dictate data security and privacy. It’s less about memorizing rules and more about adopting a specific mindset—one that revolves around risk, hard evidence, and control effectiveness.
Your entire career will be built on this foundation.
At the heart of every single SOC 2 audit are the Trust Services Criteria (TSC), the rulebook developed by the AICPA. These are the five pillars that define a trustworthy service. While all five are important, you’ll quickly learn that Security (also known as the Common Criteria) is the mandatory starting point for every engagement. No exceptions.

Unpacking the Five Trust Services Criteria
Think of the TSCs as different lenses for evaluating a company’s systems. Each one answers a different, critical question about the service they provide. A seasoned auditor knows precisely which criteria to apply based on the client’s business model and the promises they’ve made to their own customers.
- Security: Is the system protected against unauthorized access, both physical and logical? This is the non-negotiable foundation of any report.
- Availability: Is the system actually up and running as promised? This is all about uptime SLAs, redundancy, and disaster recovery plans.
- Processing Integrity: Does the system do what it says it will do—completely, accurately, and on time? This is huge for financial platforms or any service that crunches data.
- Confidentiality: Is sensitive business information (like intellectual property) protected as agreed? This goes beyond general security to cover specifically designated confidential data.
- Privacy: How is personal information handled from collection to deletion? This aligns with privacy notices and regulations like GDPR or CCPA.
A client might not need all five. In fact, a huge part of the job is helping them scope the audit to what’s relevant. A simple cloud storage service might focus on Availability and Confidentiality. A payment processor, on the other hand, must prove Processing Integrity.
Essential Audit Methodologies and Control Testing
Knowing the TSCs is step one. Knowing how to actually test them is what makes you an auditor. This is where audit methodology comes in—it’s the structured, repeatable process you use to gather evidence and form your professional opinion.
Your days will be filled with executing specific control testing procedures. These are your tools for validating whether a control is real or just shelf-ware.
The main techniques are:
- Inquiry: Asking sharp questions to the right people. You’ll interview everyone from junior engineers to the CTO to understand how things really work.
- Observation: Literally watching a process happen. This could be sitting in on an employee onboarding session to see how system access is granted.
- Inspection: This is the bread and butter. You’ll spend countless hours examining documents, system logs, firewall rules, and change management tickets.
- Re-performance: Doing the control yourself to see if you get the same result, like independently running a user access report.
Each technique builds your body of evidence. For a deeper dive, our guide on a robust internal control procedure shows how these fit into the bigger picture.
Your opinion as an auditor is only as credible as the evidence backing it up. The core loop of this job is inspecting a system log, cross-referencing it with a policy document, and then confirming the process through an interview. Get good at that, and you’ll go far.
From Theory to Practical Application
So, how do you get this knowledge? Start by burying yourself in the source material—the AICPA’s official guidance on the TSCs is your bible. But real learning only happens when you connect those abstract points to real-world scenarios.
Let’s say you’re auditing the Confidentiality of a SaaS platform. Your audit plan won’t just say “check encryption.” It gets granular.
- Inspect the cloud provider’s console to verify that data-at-rest is encrypted with AES-256.
- Review the company’s data classification policy. Does it even define what “confidential” means?
- Inquire with the DevOps lead about their key management and rotation process.
- Observe the HR manager perform the termination process to ensure system access is revoked immediately.
That’s the level of detail required. Each step is a deliberate action designed to collect concrete proof. Mastering this process—translating a high-level criterion into a list of specific, testable actions—is what separates the rookies from the pros.
Gaining Essential Hands-On Experience
Knowing the Trust Services Criteria in theory gets your foot in the door. But hands-on experience is what actually makes you a SOC 2 auditor. You can’t learn this job from a textbook. The real education happens when you’re trying to make sense of a mountain of firewall logs or interviewing a stressed-out engineer who just wants to get back to coding. This is where you learn to connect abstract control concepts to messy, real-world systems.
The path to getting this experience isn’t a single-lane highway. There are a few well-trodden entry points that can drop you right into the world of SOC 2, each giving you a unique perspective and skillset.

Common Pathways to Practical Skills
The two most established routes are through a public accounting firm or by joining an internal audit team at a tech company. Each path is a distinct training ground for an aspiring SOC 2 pro.
- Public Accounting (Risk Advisory): Joining a firm’s IT audit or risk advisory practice is the classic start. You’ll see dozens of clients, industries, and control environments in a very short time. This path is like a bootcamp for understanding different business models and control frameworks, giving you a broad base of knowledge fast.
- Internal Audit (Tech Company): Working on the inside gives you a deep, focused view of a single, complex environment. You get an insider’s look at how controls are actually built, managed, and monitored day-to-day—an invaluable perspective when you later have to audit other companies.
Both roles will immerse you in the fundamentals, especially testing IT General Controls (ITGC), which are the bedrock of any IT audit. You’ll spend countless hours digging into user access reviews, change management tickets, and IT operations—skills that map directly to the Security criterion in every single SOC 2 report.
From Junior Analyst to SOC 2 Contributor
Let’s play out a realistic scenario. You’ve just landed an entry-level gig in a risk advisory practice. Your first big project is helping a growing fintech startup with their SOC 2 readiness assessment. This isn’t the formal audit yet; it’s the prep work where you help the client find and fix gaps before the real auditors show up.
Your manager asks you to evaluate their logical access controls. Here’s what your week might look like:
- Monday: You start by reading the company’s access control policy. Does it define roles? Does it mandate quarterly reviews? You take notes, highlighting every vague statement.
- Tuesday & Wednesday: You spend hours with the IT manager, who walks you through their process for onboarding and offboarding employees. You request evidence for a sample of five new hires and five terminated employees from the last quarter.
- Thursday: The evidence arrives. You meticulously compare the HR records to the access logs for their core application and cloud infrastructure. You find that one terminated employee’s access was revoked three days late. Bingo. That’s a clear control failure.
- Friday: You document your findings, complete with screenshots and log excerpts, and write it up for your manager. You’ve just performed your first real control test and found a legitimate gap.
This one exercise teaches you more than a whole textbook. You learn about evidence collection, why timeliness matters, and how to communicate a deficiency without sounding like a jerk. This is the core loop of an auditor’s work.
Why Hands-On Work Is the Differentiator
Practical experience is what separates the SOC 2 specialists who command premium fees from the generalists. This is especially true in a market where a Type 2 audit can cost a startup anywhere from $20,000 to $60,000. The auditor’s fee alone often makes up $10,000 to $30,000 of that total. Entry-level auditors often cut their teeth at boutique or mid-market firms, which provide amazing exposure to a wide range of client needs and systems. For a closer look at the numbers, you can dive into the SOC 2 compliance cost breakdown to see how firm size and scope impact pricing.
Ultimately, your goal is to build a portfolio of these experiences. Every control you test, every client meeting you sit in on, and every report you help write adds another layer to your expertise. That accumulated wisdom is what will eventually empower you to lead your own SOC 2 engagements with confidence.
Choosing and Earning Your Key Certifications
In the world of SOC 2, your hands-on experience is what builds real expertise. But certifications? They’re the credentials that get you in the door. Think of them as the universal language that tells hiring managers you have a specific, validated skill set—and that you’re serious about this career path.
Without the right letters after your name, your path to becoming a trusted SOC 2 auditor will be a much steeper climb. These credentials aren’t just resume fluff; they prove you’ve mastered complex topics, passed a tough exam, and met specific experience requirements. They’re often the deciding factor that lands you the interview.

The “Big Four” Credentials That Matter Most
While a handful of certifications can add value, a few stand out as the heavy hitters in the SOC 2 space. Each one has a slightly different angle, so understanding the distinctions is key to picking the right one for your background and career goals.
Here are the certifications that pop up most often on job descriptions:
- Certified Information Systems Auditor (CISA): This is the global gold standard for IT audit. The CISA is all about assessing vulnerabilities, reporting on compliance, and evaluating controls. It aligns almost perfectly with the day-to-day grind of a SOC 2 auditor.
- Certified Public Accountant (CPA): Don’t forget, SOC 2 is an attestation standard from the AICPA. The CPA license provides a deep, foundational understanding of attestation principles, ethics, and reporting standards. Many firms still require a CPA to lead engagements and sign off on reports.
- Certified Information Systems Security Professional (CISSP): If the CISA is about auditing systems, the CISSP is about designing and managing them. It’s a technical powerhouse, proving deep security expertise. This one is a fantastic complement for auditors diving into highly complex tech environments.
- Certified in Risk and Information Systems Control (CRISC): As the name implies, the CRISC is laser-focused on IT risk management. It shows you know how to identify and manage enterprise IT risk and implement the controls to mitigate it—a massive part of any SOC 2 audit.
A Strategic Comparison of Top Credentials
So, which one should you tackle first? It really depends on where you’re coming from. An accountant pivoting into tech audit will naturally lean toward the CPA, while a seasoned IT pro will find the CISA or CISSP a more direct fit.
To help you decide, here’s a quick breakdown of how these top-tier certifications stack up.
Top Certifications for SOC 2 Auditors Compared
| Certification | Governing Body | Primary Focus | Best For |
|---|---|---|---|
| CISA | ISACA | Information Systems Auditing, Control, Assurance | Aspiring IT auditors looking for the most direct path into a SOC 2 role. It’s the quintessential audit cert. |
| CPA | AICPA | Accounting, Attestation Standards, Financials | Accountants who want to lead SOC 2 engagements and have the authority to sign reports. |
| CISSP | (ISC)² | Information Security Management, Technical Design | Experienced security pros who want to prove deep technical knowledge. A huge asset for senior-level auditors. |
| CRISC | ISACA | IT Risk Management, Control Implementation | Professionals who specialize in identifying and mitigating risk within IT systems. Great for risk advisory. |
Ultimately, the best certification is the one that fills the gap between your current experience and the job you want next.
The Real-World Impact on Your Career and Wallet
Earning these credentials is a serious investment of time and money, but the ROI is undeniable. In a market where a single SOC 2 Type 2 audit can run anywhere from $30,000 to $80,000, the auditor’s own qualifications can drive a huge chunk of that cost. While the CPA remains a classic, top-tier auditors often add a CISA or CISSP to their toolkit, which directly translates to higher billing rates and more senior roles.
Passing the exam is just the starting line. Every major certification requires you to earn Continuing Professional Education (CPE) credits each year to stay active. This isn’t just bureaucracy—it forces you to stay current on new threats, evolving tech, and updated standards. In this field, that’s non-negotiable.
You’ll earn CPEs by attending industry conferences, taking specialized training, or even just joining webinars. It’s a fantastic way to network while deepening your expertise in niche areas like cloud security or privacy frameworks. To see how it all works, our guide to the SOC 2 auditor certification process breaks it down.
Just remember: your first certification isn’t the end of your education. It’s the beginning of a lifelong learning process that defines a successful career in audit.
Navigating the Job Market and Landing Your First Role
You’ve got the knowledge, you’ve earned the certs—now it’s time to actually get paid for it. The good news is the SOC 2 audit job market is hot. The challenge? Landing the right first role requires a plan, not just a pile of applications.
Your first big decision is where to apply. Your options generally fall into two buckets: a massive “Big Four” accounting firm or a specialized boutique practice. The path you choose sets the tone for your early career.
The Big Four—Deloitte, PwC, EY, KPMG—offer a very structured, almost university-like environment. You’ll get incredible training, a clear-cut promotion ladder, and exposure to enormous enterprise clients across every industry imaginable. The name on your resume opens doors, period.
On the flip side, specialized firms offer a more entrepreneurial vibe. You’ll work on smaller teams, get your hands dirty with more responsibility much faster, and see your direct impact on fast-growing tech and SaaS clients. The work is often more agile, and you can carve out a niche in hot areas like cloud security or privacy.
Crafting a Resume That Gets Noticed
Let’s be blunt: your resume is a sales document, and it has about six seconds to make a sale. Before a human even sees it, you have to get past the robots. That’s why understanding optimizing your resume for ATS filters is non-negotiable. Don’t let a formatting error kill your chances.
The single biggest mistake I see on junior auditors’ resumes is vagueness. You have to quantify your experience. “Assisted with control testing” is a waste of space. It tells me nothing.
Let’s fix it:
-
Instead of: “Helped with user access reviews.”
-
Try this: “Analyzed user access permissions for 15 critical systems, validating the principle of least privilege for over 500 user accounts.”
-
Instead of: “Assisted with control testing.”
-
Try this: “Tested over 50 key controls across the Security and Availability TSCs for a SaaS client, identifying three design deficiencies that were remediated before the audit period.”
See the difference? You’ve gone from a passive helper to an active contributor who gets results.
Nailing the Technical Interview
Once you get the interview, the game changes. They know you have the basics down; now they want to see how you think on your feet.
The goal of a technical interview isn’t just to see if you know the answer. It’s to see how you think. They want to understand your process for breaking down a problem, gathering evidence, and forming a logical conclusion.
You’ll get hit with practical, scenario-based questions. They want to see you apply the Trust Services Criteria to a real-world mess.
A hiring manager might ask:
- “A client has no formal employee offboarding process. What risks does this create, and what controls would you recommend?”
- “Walk me through the evidence you’d request to validate change management controls.”
- “How would you test a client’s disaster recovery plan?”
A weak answer to that last question is, “I’d ask for the DR plan.” A rock-solid answer shows your methodology:
- Inspect: “First, I’d inspect the DR plan itself to make sure it’s documented, formally approved, and has been updated within the last year.”
- Inquire: “Next, I’d interview the system owner to confirm they understand their role and responsibilities during a DR event.”
- Validate: “Finally, I’d request the results from the latest DR test—the test script, the outcome report, and any post-mortem notes—to verify the plan actually works in practice.”
This shows you think like an auditor: inspect, inquire, validate.
Understanding Salary and Compensation
Your earning potential grows quickly in this field. While the numbers shift based on location and the size of the firm, here’s a realistic look at what you can expect.
-
Entry-Level/Associate (0-2 years): You’ll likely start in the $65,000 - $85,000 range. Your entire job is to learn the audit process and get really good at detailed control testing.
-
Senior Auditor (3-5 years): After earning a CISA or CPA, you’re looking at $90,000 - $125,000. At this stage, you’re leading smaller audits and starting to mentor the new associates.
-
Manager/Senior Manager (5+ years): This is where compensation jumps significantly, often exceeding $140,000+. Your focus shifts to managing client relationships, scoping new projects, and developing the practice.
Knowing these benchmarks is key for negotiating your offers and mapping out your career. If you’re trying to get a feel for what different firms focus on, checking out their public-facing SOC audit services can give you clues about their client base and specialties.
Answering Your Top Questions About a SOC 2 Career
Even with a clear roadmap, you probably have some lingering questions about what this job really feels like on the ground. Let’s tackle the most common ones I hear from aspiring auditors to give you the clarity you need.
What Does a SOC 2 Auditor Actually Do All Day?
Forget the stereotype of a lone wolf crunching numbers in a dark room. While deep-focus work is part of the job, a typical week is a dynamic mix of technical analysis, client interaction, and meticulous documentation.
Your time is generally split across three core activities:
- Evidence Review: This is the heart of the job. You’ll spend a significant chunk of your time combing through evidence—everything from firewall configurations and IAM policies to background check records and change management tickets in Jira.
- Client Communication: You are constantly in touch with your clients, mostly over email and video calls. You’ll be requesting documents, asking clarifying questions, and walking engineers through exactly what you need to see and why.
- Documentation: If you didn’t document it, it didn’t happen. Every test you run needs a clear write-up detailing the procedure, linking to the specific evidence, and stating your conclusion: did the control pass or fail?
A common misconception is that this is a purely technical role. In reality, it’s about 50% technical analysis and 50% communication and project management. You have to be as good at writing a clear email as you are at reading a system log.
How Long Does It Realistically Take to Get Certified?
This depends entirely on which certification you’re chasing and where you’re starting from. Let’s focus on the CISA (Certified Information Systems Auditor), since it’s the gold standard for this career path.
ISACA, the body that governs the CISA, requires a minimum of five years of relevant work experience in information systems auditing, control, or security. But there are waivers that can shorten this. For example, a relevant bachelor’s degree can knock off up to two years of that requirement.
Most people I know spent a solid 3-6 months of dedicated study time just for the CISA exam. So, a realistic timeline from landing your first eligible job to actually having “CISA” in your email signature is often in the 3-to-4-year range.
What’s the Real Difference Between a SOC 2 Type 1 and Type 2 Audit?
Knowing this cold is non-negotiable in an interview, and it dictates the entire rhythm of your work. The difference boils down to one thing: time.
- A SOC 2 Type 1 report is a snapshot. It assesses the design of a company’s controls at a single point in time. Your job is to answer the question: “On October 26th, did the company have the right controls in place to meet the criteria?”
- A SOC 2 Type 2 report is a feature film. It assesses the operating effectiveness of those controls over a period of time, usually 6 to 12 months. This is where the real work is. You’re not just checking if a control exists; you’re proving it worked, consistently, for the entire period.
For a Type 2, you’re doing a lot of sampling. To test employee offboarding, for instance, you won’t just look at one person. You’ll test a sample of all employees who left over the last six months to prove their access was revoked on time, every single time. This is why a Type 2 report carries so much more weight with customers.
Is It Better to Come From an Accounting or IT Background?
Honestly, there’s no “better” starting point. Both accounting and IT pros can become fantastic auditors. The key is your willingness to learn the other side’s language.
| Background | Strengths in SOC 2 Auditing | Areas for Development |
|---|---|---|
| Accounting/Finance | You live and breathe attestation standards, risk assessment, and audit methodology. Your documentation and report writing skills are probably top-notch. | You’ll need to get your hands dirty with the tech. This means learning about cloud infrastructure, network security, and the software development lifecycle. |
| IT/Cybersecurity | You have immediate credibility with engineering teams. You understand the systems, the controls, and the security frameworks they’re built on. | You have to learn the formal audit process—how to document evidence properly, write test procedures, and navigate the AICPA’s strict attestation rules. |
The best auditors I’ve worked with are bilingual. They can talk attestation standards with a CFO in the morning and then jump on a call to debate cloud security groups with a DevOps engineer in the afternoon. Your goal isn’t to stay in your lane; it’s to build a bridge between them.
Finding the right audit firm is a critical first step in your journey. At SOC2Auditors, we make the process simple. Our platform helps you compare over 90 verified firms based on real pricing, timelines, and client satisfaction so you can find the perfect match for your career goals. Get started at https://soc2auditors.org.