Difference between a soc1 and soc2 report: Key Differences and When to Use Each

The real difference between SOC 1 and SOC 2 comes down to one simple question: What are you trying to prove, and to whom?
A SOC 1 report focuses on controls that could impact your client’s financial statements. In contrast, a SOC 2 report looks at controls related to data security, availability, confidentiality, and privacy. Think of it as financial diligence versus operational security.
Understanding the Core Difference SOC 1 vs SOC 2
Choosing the right report is one of the first major compliance hurdles a service organization faces. Get it wrong, and you’ll waste months and thousands of dollars on an audit your customers don’t actually need. The choice hinges entirely on the service you provide and the specific assurances your clients are asking for.

Financial Controls vs. Security Controls
A SOC 1 report is all about Internal Control over Financial Reporting (ICFR). It’s built for service providers whose systems are a direct extension of their clients’ financial processes. We’re talking about payroll processors, loan servicing companies, or data centers hosting financial apps. The primary audience is your client’s financial auditors and controllers, who need to trust that your service won’t mess up their books.
On the other hand, a SOC 2 report is built on the AICPA’s Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. This makes it the undisputed standard for tech companies—think SaaS providers, cloud hosting services, and HealthTech platforms. Its audience is much broader, including potential customers, partners, and CISOs who need solid proof that you can protect their data.
In fact, a recent BizTech survey showed that 65% of enterprise procurement decisions now demand a SOC 2 Type 2 report. That number has shot up dramatically in just the past few years, making it a non-negotiable for anyone selling to larger companies.
To make it even clearer, here’s a quick side-by-side comparison.
SOC 1 vs SOC 2 At a Glance
This table offers a high-level summary of the key distinctions between SOC 1 and SOC 2 reports, covering their primary purpose, target audience, governing standards, and the core focus of the audit.
| Attribute | SOC 1 Report | SOC 2 Report |
|---|---|---|
| Primary Purpose | Audits controls impacting clients’ financial reporting (ICFR). | Audits controls based on Trust Services Criteria. |
| Target Audience | Client’s financial auditors, controllers, and finance teams. | Clients, prospects, procurement teams, and CISOs. |
| Governing Standard | SSAE 18 (Attestation Standards). | AICPA’s Trust Services Criteria (TSC). |
| Core Focus | Financial transaction integrity and accuracy. | Data security, availability, confidentiality, and privacy. |
At the end of the day, both reports are about validating your internal controls. To get a better handle on what that entails, it’s worth digging into modern internal control best practices.
Ultimately, nailing the distinction between financial focus (SOC 1) and operational security focus (SOC 2) is the single most important step in choosing the right compliance path for your organization.
Comparing Audit Scope and Criteria
The real difference between a SOC 1 and a SOC 2 report isn’t just their purpose—it’s in the very DNA of the audit itself. They look at completely different sets of controls, which dictates everything from the evidence you’ll need to pull to the framework you follow. Getting this distinction right from the start is crucial.
A SOC 1 audit has a laser focus on one thing: Internal Control over Financial Reporting (ICFR). The auditor’s entire job is to look at the controls that could realistically impact your client’s financial statements. It’s not a general security audit; it’s all about the integrity of financial data processing.
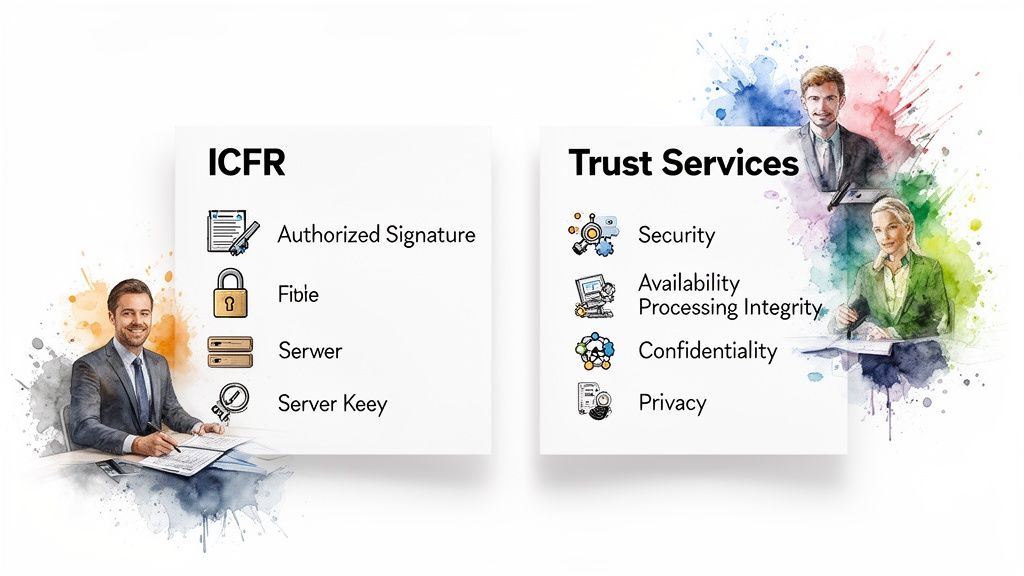
The SOC 1 Focus: Internal Control Over Financial Reporting
Everything in a SOC 1 audit is measured by its potential financial impact. Auditors will zero in on controls that ensure transactions are handled correctly and securely from start to finish.
Here are a few real-world examples of SOC 1 controls:
- Transaction Authorization: These are the rules ensuring every financial transaction your system touches has the right approval. For a payroll provider, this might mean having a control to verify that a client’s HR manager explicitly authorized a pay raise.
- Access to Financial Systems: This covers the procedures that lock down sensitive financial apps and data. Think logical access controls, regular user account reviews, and managing who has admin rights to systems that handle billing or invoicing.
- IT General Controls (ITGCs): These are the foundational IT controls that support the financial applications. This includes things like change management for your billing system, data backup and recovery procedures, and security measures that protect the data’s integrity.
The key thing to remember about SOC 1 is this: if a control doesn’t have a clear, direct line to the financial data you process for clients, it’s probably not in scope. This keeps the report hyper-focused and valuable to financial auditors.
The SOC 2 Focus: The Five Trust Services Criteria
SOC 2, on the other hand, casts a much wider net. Its scope is built around the AICPA’s Trust Services Criteria (TSC), a set of principles used to evaluate how well you manage and protect customer data in general. The great thing about SOC 2 is its flexibility; you choose the criteria that matter most for your services and the promises you’ve made to customers.
The five Trust Services Criteria are:
- Security (Required): Often called the Common Criteria, this is the non-negotiable foundation of every single SOC 2 report. It’s all about proving your system is protected against unauthorized access, use, or changes.
- Availability (Optional): This one evaluates whether your systems are up and running as promised. It’s critical for services where any downtime spells disaster for clients, like a cloud hosting platform or a mission-critical SaaS tool.
- Processing Integrity (Optional): This is for businesses that need to prove their system processing is complete, valid, accurate, and on time. An e-commerce platform processing thousands of transactions or a complex data analytics service would absolutely want to include this.
- Confidentiality (Optional): This criterion is about protecting information that’s specifically designated as confidential. It’s a must-have for organizations handling sensitive business data, intellectual property, or strategic plans for their clients.
- Privacy (Optional): Don’t confuse this with Confidentiality. Privacy is strictly about the collection, use, retention, and disposal of personal information (PII). It lines up with regulations like GDPR and CCPA, making it vital for any company handling consumer data.
Your choice of TSCs directly shapes the entire audit. While Security is always there, adding Availability or Confidentiality will significantly expand the number of controls an auditor needs to test. If you want to dig deeper into the specific controls and procedures an auditor might look at, a good cyber security audit checklist can give you a better feel for what’s involved.
Ultimately, the choice between SOC 1 and SOC 2 boils down to financial precision versus broad operational security.
Understanding Type 1 vs Type 2 Reports
Beyond the SOC 1 vs. SOC 2 decision, there’s another critical layer: Type 1 versus Type 2. Both SOC reports come in these two flavors, and getting this choice wrong can mean delivering an audit report that your customers simply won’t accept.
It really boils down to a snapshot versus a movie.
A Type 1 report is that single snapshot in time. A Type 2 is the full-length film showing your security controls in action over months.
Type 1 Reports: The Point-in-Time Snapshot
A Type 1 report evaluates the design suitability of your controls on a specific date. An auditor comes in, reviews your documentation and processes, and confirms that—on paper—your controls are designed correctly to meet your objectives. That’s it.
The question it answers is: “Are our controls structured correctly right now?”
This makes it a faster and less expensive option, which can be a smart strategic move. For instance, a startup might get a Type 1 to satisfy an urgent request from its first big enterprise customer. It acts as a solid first step, showing you’ve designed a thoughtful control environment, even before you can prove it works over the long haul.
Type 2 Reports: The Gold Standard of Assurance
A Type 2 report, on the other hand, assesses the operating effectiveness of your controls over a period of time, usually between six and twelve months. This is a much deeper, more rigorous audit. Auditors aren’t just looking at the design; they are actively testing your controls to gather evidence that they worked consistently throughout the entire review period.
This report answers the far more powerful question: “Did our controls actually work as intended over the last year?” That historical proof is exactly why Type 2 reports are the industry gold standard and what sophisticated enterprise clients now demand.
A Type 1 report shows you have a plan. A Type 2 report proves your plan works in the real world. For customers entrusting you with critical data or processes, that proof is non-negotiable.
While both SOC 1 and SOC 2 offer these types, the real-world demand is clear. A SOC 1 Type 2 is critical for demonstrating sustained control over financial processes for things like SOX compliance. Meanwhile, a SOC 2 Type 2 has become the undisputed benchmark for tech companies. Data shows that 85% of HealthTech and FinTech RFPs now specify a SOC 2 Type 2, a figure that’s only grown with increasing regulatory pressure.
Making the Strategic Choice
Choosing between Type 1 and Type 2 is a business decision, not just a compliance one. A Type 1 can be a useful stepping stone, but the market has already spoken. Most mature customers will eventually require the higher assurance that only a Type 2 report provides.
Here’s a simple way to break it down:
- Choose a Type 1 if:
- You’re brand new to SOC compliance and need a foundational report fast.
- A key prospect has an urgent request and you don’t have the months needed for a Type 2 observation period.
- You want to validate your control design before committing to a full-blown Type 2 audit.
- Choose a Type 2 if:
- Your clients are enterprise-level and need proof of long-term operational effectiveness.
- You’re in a competitive market where a Type 2 is a key differentiator that closes deals.
- You handle highly sensitive data and must provide the strongest assurance possible.
For a more detailed breakdown, check out our guide on the differences between SOC 2 Type 1 and Type 2 reports. Ultimately, your choice signals to the market just how seriously you take your security commitments.
Which Report Do You Need? Industry Use Cases
The theoretical stuff is great, but the real decision between SOC 1 and SOC 2 clicks when you see how it solves actual business problems. The right choice boils down to the service you offer, your industry, and—most importantly—what your clients are trying to protect.

Let’s walk through how this plays out in three key tech sectors. You’ll see a clear progression from a pure focus on financial controls to an absolute need for airtight data protection.
FinTech: The Non-Negotiable SOC 1
For most FinTech companies, the choice is made for you. If your platform is a critical gear in your client’s financial machinery, a SOC 1 report isn’t a “nice-to-have.” It’s your ticket to the game.
- Use Case: A payment processing platform that handles merchant transactions, fee calculations, and payouts.
- Business Problem: Their customers—e-commerce businesses—depend on the platform for accurate revenue reporting. An error in transaction processing directly messes with their financial statements.
- Key Stakeholders: The client’s CFO, their finance team, and their external financial auditors. These people need to prove your internal controls are solid enough to prevent material errors on their books.
- Why SOC 1 is Correct: A SOC 1 report directly addresses Internal Control over Financial Reporting (ICFR). It’s built to examine the very controls financial auditors care about: transaction authorization, data accuracy, and system calculations.
- Consequence of the Wrong Report: Handing them a SOC 2 is like bringing a basketball to a soccer match. It proves you have security, but it says zero about financial accuracy. The client’s auditors would have a massive hole in their evidence, which could kill the deal or force them to do their own expensive audit of your systems.
B2B SaaS: The Essential SOC 2
For the vast majority of B2B SaaS companies, your promise isn’t about financial reporting. It’s about delivering a secure, reliable, and available service. This is home turf for the SOC 2 report; it’s the undisputed industry standard.
- Use Case: A cloud-based project management tool where enterprise teams manage sensitive product roadmaps and confidential client data.
- Business Problem: The customer needs rock-solid assurance that their intellectual property won’t be leaked and that the service won’t go down during a critical launch.
- Key Stakeholders: The customer’s CISO, their IT department, and the procurement team. Their world revolves around operational risk and data governance, not your impact on their balance sheet.
- Why SOC 2 is Correct: A SOC 2, scoped with the Security and Availability Trust Services Criteria, is a direct answer to their concerns. It’s independent proof that you have real controls for access, network security, and incident response, and that you can actually deliver on your uptime promises.
- Consequence of the Wrong Report: A SOC 1 would be completely irrelevant. It offers no meaningful information about data security or system availability, failing to answer the most fundamental questions from security and procurement teams.
The choice of report is a direct reflection of the promise you make to your customers. For FinTech, the promise is financial accuracy. For SaaS, it’s data security and operational reliability. Your compliance report must validate that specific promise.
HealthTech: The Critical SOC 2 with Privacy
In healthcare, data protection is non-negotiable and legally mandated. The moment you handle Protected Health Information (PHI), the scrutiny intensifies, making a specific flavor of SOC 2 an absolute must.
- Use Case: A patient portal software that stores and transmits electronic health records (EHR) between patients and hospital systems.
- Business Problem: This company is a steward of incredibly sensitive PHI, which is regulated by HIPAA. Hospital clients must ensure their vendors have bulletproof controls to prevent data breaches and protect patient privacy.
- Key Stakeholders: The hospital’s compliance officer, legal counsel, and risk management team. They need definitive proof that your controls align with HIPAA’s Security and Privacy Rules.
- Why SOC 2 is Correct: SOC 2 is the perfect framework, but it has to be scoped correctly. It is critical to include not just Security and Availability, but also the Confidentiality and Privacy Trust Services Criteria. This combination gives specific assurance that PHI is shielded from unauthorized eyes and managed according to strict privacy principles.
- Consequence of the Wrong Report: A SOC 1 isn’t even in the same universe. Even a basic SOC 2 focused only on Security is insufficient because it misses the specific requirements for PHI. Lacking a SOC 2 with the Privacy and Confidentiality criteria is a massive red flag that would likely get a vendor disqualified on the spot due to HIPAA compliance risks.
Navigating SOC Audit Timelines and Costs
Let’s talk about the two things everyone wants to know: how long is this going to take, and what’s it going to cost? Planning for a SOC 1 or SOC 2 audit requires a real investment of time and money. Knowing the benchmarks upfront helps you set expectations and avoid sticker shock. This isn’t just a checklist—it’s a marathon that rewards good preparation.
The biggest factor driving your timeline is whether you’re going for a Type 1 or Type 2 report. A Type 1 audit is a snapshot in time, looking at the design of your controls, so it’s naturally faster. A Type 2, on the other hand, tests if those controls actually work over a period of time, making it a much longer commitment.
Typical Timelines for SOC Audits
For any company going through this for the first time, the journey starts with a readiness assessment. Plan for this to take anywhere from two to six weeks. This is your chance to find and fix the gaps in your controls before the auditors start the clock on their formal engagement. It’s the single most valuable step you can take for a smooth audit.
After that initial phase, the paths for Type 1 and Type 2 diverge significantly:
- Type 1 Report: Once you’ve completed the readiness work, a Type 1 audit can be wrapped up, report in hand, in about six to ten weeks. Its speed makes it a great option if you have an urgent customer request breathing down your neck.
- Type 2 Report: The game-changer here is the observation period. After you’re ready, your controls have to run consistently for a set period, usually six to twelve months. The auditors can only begin their testing after this period ends, which adds another four to eight weeks for fieldwork and reporting.
All in, a first-time Type 2 report can easily take nine to eighteen months from start to finish. For a phase-by-phase breakdown, check out our guide on how long a SOC 2 audit takes.
A thorough readiness assessment is the single best investment you can make in the SOC audit process. Identifying and remediating control gaps upfront can prevent costly delays and the dreaded ‘qualified’ opinion that undermines the entire effort.
Understanding the Cost Factors
There’s no single price tag for a SOC audit. Costs for a SOC 2 report, for instance, can swing from $15,000 to well over $100,000. The final number comes down to a few key variables, and understanding them will help you make sense of the quotes you receive.
Here are the main drivers that influence the final price:
- Audit Firm Selection: A boutique, specialist CPA firm will have a different price point than a “Big Four” accounting firm. You’re often paying for brand recognition with the latter.
- Company Size and Complexity: It’s simple math. A larger company with more employees, more systems, and multiple office locations has a more complex control environment, which means more for the auditors to test.
- Audit Scope: This is a big one for SOC 2. The number of Trust Services Criteria (TSCs) you include directly impacts the cost. An audit focused only on the mandatory Security criterion will be much cheaper than one that also adds Availability, Confidentiality, and Privacy.
- Remediation Effort: If your readiness assessment uncovers major gaps, the internal time and potential consulting fees to fix everything will add to your total investment before the audit even officially kicks off.
In the end, both your timeline and your budget are directly tied to how prepared you are. A well-documented, mature control environment will always result in a faster, more cost-effective audit.
Making the Right Choice for Your Business
Figuring out whether you need a SOC 1 or a SOC 2 report boils down to a few critical business questions. Your choice isn’t just about compliance costs—it directly impacts your ability to close deals and build trust with the right audience. Getting this right from the start saves a lot of headaches later.
First, who is actually asking for the report, and what do they really care about? If the request is coming from your client’s financial auditors or CFO, their world revolves around Internal Control over Financial Reporting (ICFR). But if CISOs, security teams, and procurement departments are the ones asking, their concerns are all about data security, privacy, and operational resilience.
A Decision-Making Checklist
To cut through the noise, run through this simple checklist. The answers will point you directly to the report that matches your business model and, more importantly, your customer’s expectations.
- Does our service directly impact our clients’ financial statements? If you handle payroll, process payments, manage billing, or host financial applications, the answer is a hard yes. Any hiccup in your service could create a material misstatement on their books, making a SOC 1 report essential.
- What type of data do we process for our customers? If you’re storing, processing, or transmitting sensitive but non-financial data—think intellectual property, strategic plans, or personal information (PII)—then a SOC 2 report is the right move.
- What is the core promise of our service? Do you promise financial accuracy and integrity? Or do you promise security, uptime, and data protection? Your compliance report needs to validate that specific promise to be valuable.
This flowchart gives you a high-level view of the SOC audit process, from the initial readiness work to getting the final report in hand. It helps visualize the commitment you’re making.
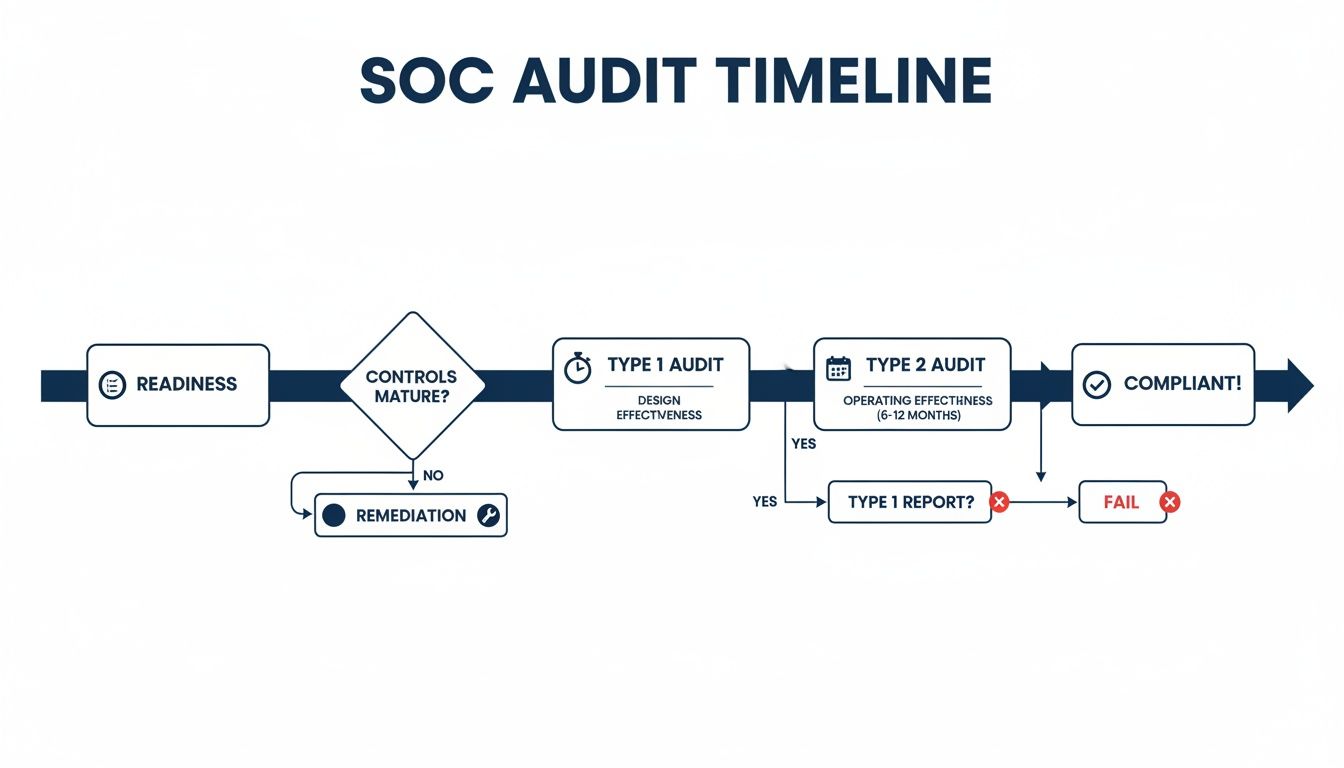
As you can see, a Type 1 report is a point-in-time snapshot that gets you a report faster. But the Type 2 report, which requires a sustained observation period, is a longer and much more robust process that provides deeper assurance.
What If You Need Both Reports?
It’s actually pretty common for a service organization to need both. A FinTech platform is a perfect example: it might process financial transactions (requiring a SOC 1) while also storing sensitive customer data in the cloud (requiring a SOC 2).
If this is you, the key is to be strategic. You don’t have to tackle both audits at once. Many companies start with the report that addresses the most immediate customer demand. A smart approach is to leverage the control environment you build for one audit to streamline the next, since many foundational security controls (like the SOC 2 Common Criteria) overlap with the IT General Controls in a SOC 1.
Your compliance roadmap should be driven by customer demand and market positioning. Start with the report that unblocks your most significant revenue opportunities, and build from there.
Choosing the right path starts with understanding your service’s impact. However, the success of your audit also depends heavily on the firm you partner with. Finding the right partner is crucial, which is why it’s important to understand how to select a reputable SOC 2 audit firm that matches your company’s size, industry, and budget. An experienced auditor provides invaluable guidance and ensures your final report truly meets stakeholder expectations.
Common Questions About SOC 1 vs. SOC 2
When you’re navigating compliance, a lot of specific questions come up. Here are some straight answers to the most common queries we hear about SOC 1 and SOC 2 reports.
Can a Company Have Both a SOC 1 and SOC 2 Report?
Yes, and honestly, it’s becoming pretty standard, especially for FinTech companies. It happens when a company’s services hit two different risk categories for their customers.
Imagine a FinTech platform that processes financial transactions—that directly impacts their clients’ financial statements, triggering the need for a SOC 1. At the same time, if they host sensitive customer data in the cloud, those customers will demand robust security assurances, which is where SOC 2 comes in. The key is that each report serves a different audience: SOC 1 is for the financial auditors, while SOC 2 is for the security, procurement, and risk teams.
Which Report is Better for a SaaS Company?
For the overwhelming majority of SaaS companies, a SOC 2 report is the right choice. It’s not even close. Most SaaS platforms simply don’t have a direct, material impact on their clients’ financial reporting in a way that would ever require a SOC 1.
The entire value proposition for a SaaS business is built on trust—providing a secure, available, and confidential service. A SOC 2 report directly addresses these operational promises. It’s the industry-standard way to prove to customers that your security and data protection practices aren’t just marketing fluff.
The core question for any SaaS business is: “What risk are we helping our customers manage?” If the answer is data security and operational uptime, then SOC 2 is the definitive answer. A SOC 1 would be completely irrelevant.
Is SOC 2 a Certification?
This is a common point of confusion. Technically, no. While you’ll hear “SOC 2 certified” and “SOC 2 compliant” all the time, a SOC 2 is an attestation report, not a certification.
Here’s why that distinction matters: a certification usually implies a simple pass/fail standard against a rigid checklist. An attestation, on the other hand, is an independent CPA firm’s formal opinion on whether your company’s unique controls are suitably designed and operating effectively to meet the criteria. It’s a much more nuanced and detailed assessment of your specific environment.
Which Report Is More Difficult to Obtain?
Neither report is inherently “harder,” but the challenges are completely different. The difficulty of a SOC 1 audit is all about depth. It’s laser-focused on financial controls, which can get incredibly complex if your systems are tightly woven into your clients’ financial workflows. The challenge is proving the integrity of those very specific transaction-level controls.
A SOC 2 audit’s difficulty comes from its breadth. A report covering only the Security criterion is certainly less demanding than one that includes all five Trust Services Criteria. The real work in a SOC 2 is documenting, implementing, and proving the effectiveness of a wide array of operational and security controls over a long period.
Finding the right auditor is just as critical as choosing the right report. At SOC2Auditors, we replace endless sales calls and confusing quotes with a data-driven matching platform. Compare real pricing, timelines, and verified client satisfaction scores from over 90 firms to find the perfect audit partner for your business. Get your tailored matches at https://soc2auditors.org.